Microsoft warns that ASP.NET machine keys found online can be misused for malware attacks. The company provides developers with recommendations to prevent such attacks.
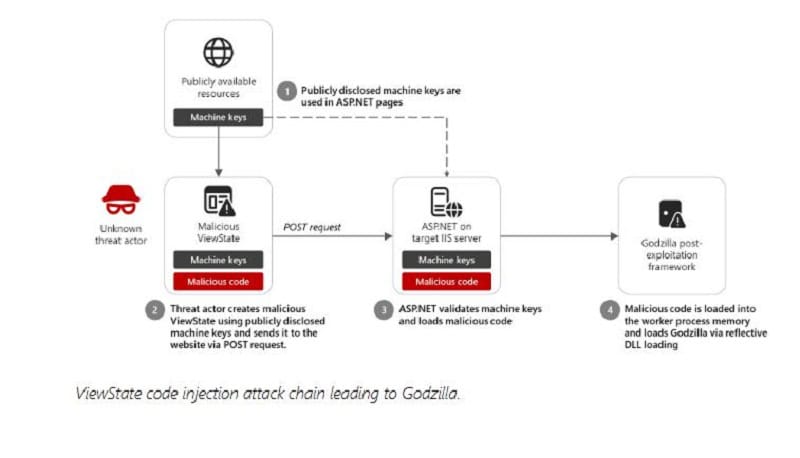
According to Microsoft, hackers are using approximately more than 3,000 available ASP.NET keys found online to carry out malware attacks. This is mainly done through so-called ViewState code injection attacks.
These ASP.NET keys are intended to protect ViewState from tampering and to prevent the release of information. The public keys found in code documentation and on repository platforms are sometimes used by developers for their own software.
Malicious use
Unfortunately, hackers can also use these keys for code injection attacks. They do this primarily to create malicious View States, which are used by ASP.NET Web Forms to check the status of and save Web pages. This can be done by adding a manipulated message authentication code (MAC).
This allows them to eventually down load the malicious ViewState data into the working memory. This enables attackers to execute code on the IIS servers to deploy other malware.
Microsoft is especially apprehensive about using these publicly found ASP.NET keys. According to the company, these now make the attack surface much larger than keys previously available on the darknet. Moreover, they can be directly applied without any modification.
Recommendations from Microsoft
To counter the danger of public ASP.NET keys, Microsoft therefore comes up with some important recommendations for developers. First, they should generate keys in a secure manner and not use default keys found online. They should also encrypt machineKey and connectionString elements to prevent access to plaintext secrets.
Other measures to be taken include upgrading apps for ASP.NET 4.8 to use the Antimalware Scan Interface (AMSI) features and better protecting Windows servers by taking measures to reduce the attack surface. These include applying rules such as Block Webshell creation for Servers.
Furthermore, Microsoft provides further detailed steps to remove or replace ASP.NET keys in the web.config configuration file. This is done by using either PowerShell or the IIS manager console. A final solution, of course, is for developers to remove key examples from their public documentation to strongly discourage insecure use.
Also read: Microsoft addresses Windows vulnerability with PowerShell script