Security specialist ESET has evidence that hackers with targeted Advanced Persistent Threats (APTs) are preparing possible attacks on power grids. The now discovered GreyEnergy malware framework has similarities with the hacker group BlackEnergy which has been systematically attacking the Ukraine for several years.
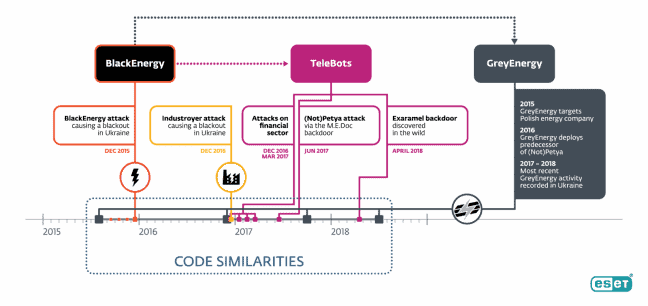
During a press event in Bratislava, Slovakia, the security specialist announced that the new extremely dangerous APTs had recently surfaced at three of its clients in the Ukraine and Poland. In the signature of the APTs, the experts saw a relationship with BlackEnergy, the group of hackers that managed to shut down the electricity grid in the Eastern European country at the end of 2015, thus causing a blackout.
APTs are cyber-attacks by hackers that combine a broad spectrum of technically complex attack weapons to achieve their goal. The attackers are going through this for a long time and are clearly focused on getting access step by step. The aim is to keep the activities under the radar for as long as possible. Finally, these hackers are very good at their job, are well organised and have ample financial resources.
Links to BlackEnergy and Telebots
What worried ESET researchers most about GreyEnergy’s discovery was that the malware discovered has links to the Telebots group. This group of malicious parties is expressly associated with the notorious NoTPetya-malware which in 2017, also via a source in the Ukraine, caused great damage to companies such as Maersk and Durex worldwide. In addition, Telebots is also linked to Industroyer, another extremely powerful malware that it has provided on the specific operating systems of industrial software.
Structure GreyEnergy malware
According to the researchers, the malware found has a modular structure. This means that the functionality of the malware depends on the combination of modules that send the attackers to the systems being attacked. ESET found modules for backdoors spying, file extraction, a way to take screenshots or do keylogging for stealing passwords and tokens. The security specialist has not found any specific modules to attack industrial software and operating systems.
The now discovered GreyEnergy malware has not yet caused any real damage. ESET’s researchers indicate that the software is clearly aimed at staying low profile and may have previously caused damage that has yet to be detected. Or it was malware that was specifically sent on a reconnaissance mission. However, the discovery shows that power companies are now also targeted and that strategic attacks on ICS workstations can be carried out using SCADA software and servers.
Russia or not
The ESET experts don’t want to lose anyone who’s exactly behind GreyEnergy. They say that they only look at the techniques used and see similarities with the BlackEnergy and Telebots attacks. They can’t tell exactly who’s carrying out the attacks. When asked whether these aggressive hackers might be supported by a nation state – Russia is often mentioned here – the experts from the security specialist were silent.
This news article was automatically translated from Dutch to give Techzine.eu a head start. All news articles after September 1, 2019 are written in native English and NOT translated. All our background stories are written in native English as well. For more information read our launch article.