More than 20,000 Linksys routers regularly leak historical data from every device that has ever connected to them. That’s what Ars Technica reports based on research by security guard Troy Mursch.
The historical overviews include MAC addresses, names and operating systems of all devices that have ever connected to the affected routers. According to Mursch, there are more than 30 different router models that are vulnerable. A search on Binary Edge, a search engine for internet-connected devices, revealed more than 21,000 vulnerable routers, which together leaked more than 756,000 unique MAC addresses.
Risk
A MAC address is a unique identifier for each network device. Mobile apps, such as smartphones and laptops, share this identifier every time they connect to a wireless network. This creates a fingerprint that can be used to track that device’s movement over networks, Mursch explains the potential risk.
If the device name also contains the full name of the owner, for example John Smith’s iPhone, the identity of the owner can be determined and it can then be located via the public IP address of the Linksys router.
In any scenario, the public leakage of the historical overview of every device ever connected to the Linksys Smart Wi-Fi router is a privacy issue that shouldn’t be taken lightly, Mursch continues. This information allows attackers to gain visibility into your home or corporate network so they can launch targeted attacks.
The vulnerable routers also leak whether or not the administrative password of the router has been changed. Of the more than 20,000 vulnerable devices found by Mursch, approximately 4,000 were still using the standard password. The routers also all have remote access enabled, allowing a hacker to quickly search for devices that can easily be taken over remotely.
Patched or not?
Linksys was notified of the leak, but is not taking any further action because, according to the company, the vulnerability was already solved with a patch in 2014.
We quickly tested the router models indicated by Bad Packets with the latest publicly available firmware (with default settings) and were unable to reproduce CVE-2014-8244, which means that it is not possible for an external attacker to use this technique to retrieve sensitive information, it sounds in a security advisory.
However, Mursch argues that the routers remain vulnerable even after the patch, even if the firewall is turned on. That his scan still found more than 20,000 vulnerable routers in the wild, means that a lot of people have either failed to update their router correctly, or that the patch indeed does not have any effect in all cases.
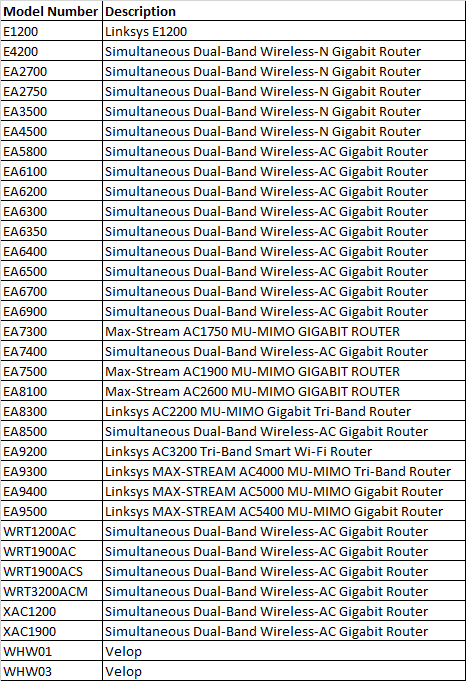
The complete list of vulnerable routers shared by Mursch can be found below. He also made an interactive overview by country. In Belgium and the Netherlands 138 and 203 vulnerable routers were found respectively. Anyone who uses one of these routers would do well to test for themselves whether the device is leaking historical data from connected devices to the Internet and, if necessary, to take further measures.