The UK’s National Health Service (NHS) has issued a warning stating that hackers are actively exploiting Log4j vulnerabilities in unpatched VMware Horizon servers.
Log4j vulnerabilities are everything but a concern of the past. The problem continues to claim victims. The UK NHS recently issued a warning for unpatched VMware Horizon servers.
The actively exploited vulnerability allows hackers to ‘drop’ malicious web shells and leave persistent malicious code within networks. This malicious code can be used for a follow-up attack at a later time.
Attack details
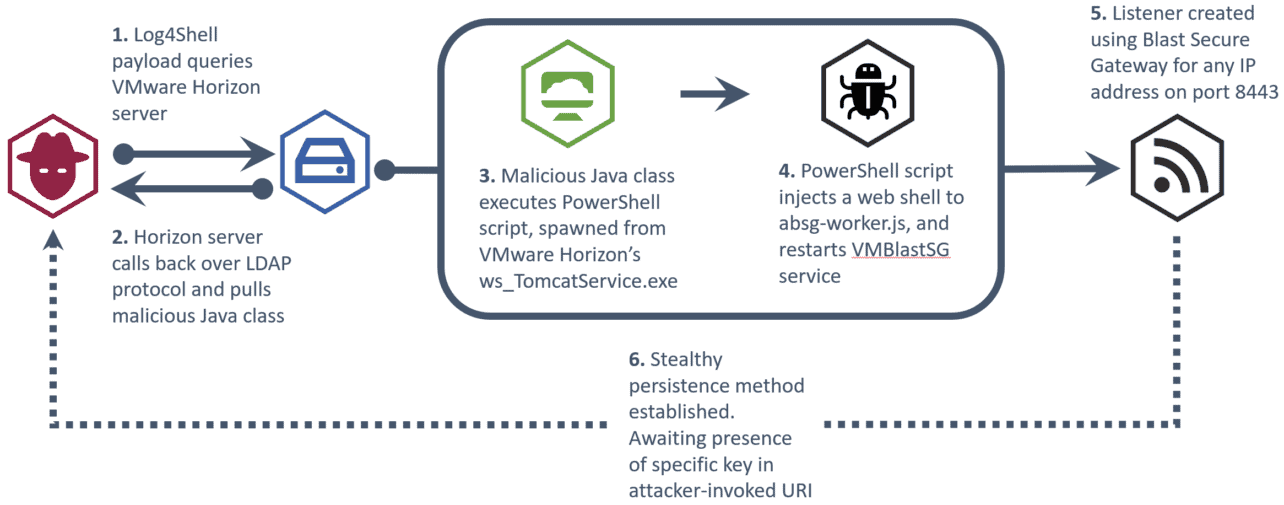
In the alert, NHS security specialists describe exactly how hackers exploit the Log4j vulnerability in VMware Horizon servers. Hackers first perform reconnaissance to find a vulnerable entry. To do this, they use the Java Naming and Directory Interface (JNDI) via Log4jShell payloads. These payloads interact with a malicious infrastructure.
Once a vulnerability is found, the attackers use a LDAP protocol to retrieve and execute a malicious Java class file. This file then injects a web shell into the VM Blast Secure Gateway Service. The web shell can then be used to perform several malicious activities, including deploying other malicious software, encrypting and stealing data.
VMWare Response
VMware Horizon versions affected by the Log4j exploit include 7.x and 8.x. The tech giant urges users of these versions to install previously available patches as soon as possible.
Not only VMware Horizon is affected by Log4j. VMware VCenter is vulnerable as well.
Tip: Security researchers find new Log4Shell in H2 database software