In a recent study, Risk Based Security concludes that the number of third-party WordPress plugins with vulnerabilities has increased significantly in the past year.
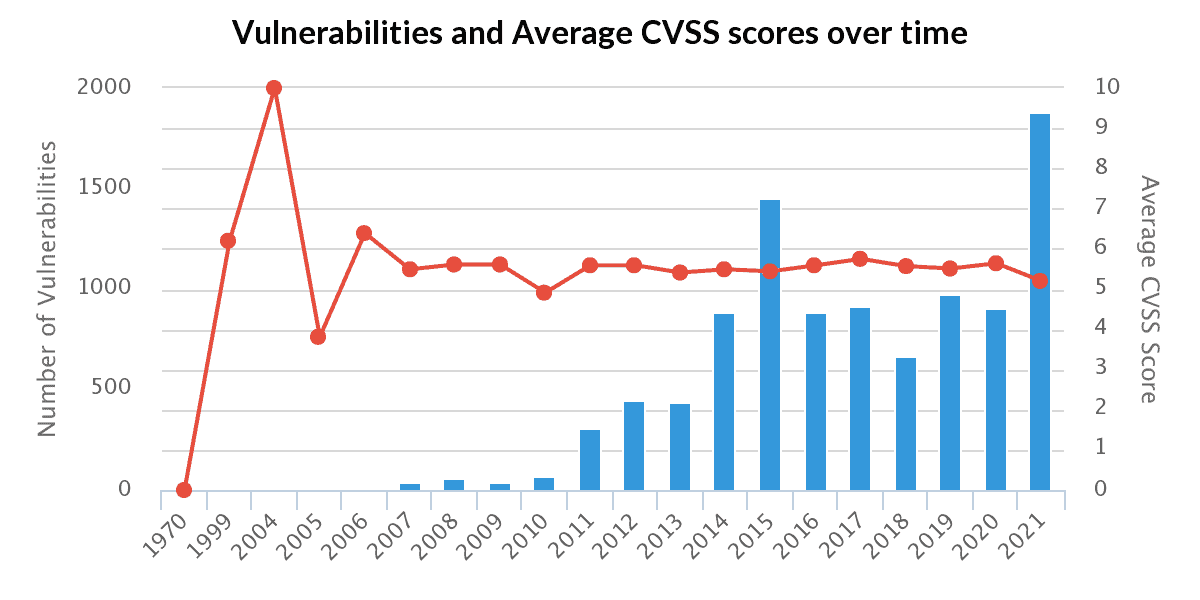
According to the security specialists, 10,359 vulnerabilities were discovered in 2021 among providers of WordPress plugins. A total of 2,240 new vulnerabilities were found in plugins in the past year. A whopping increase of 142 percent compared to 2020.
Many known exploits
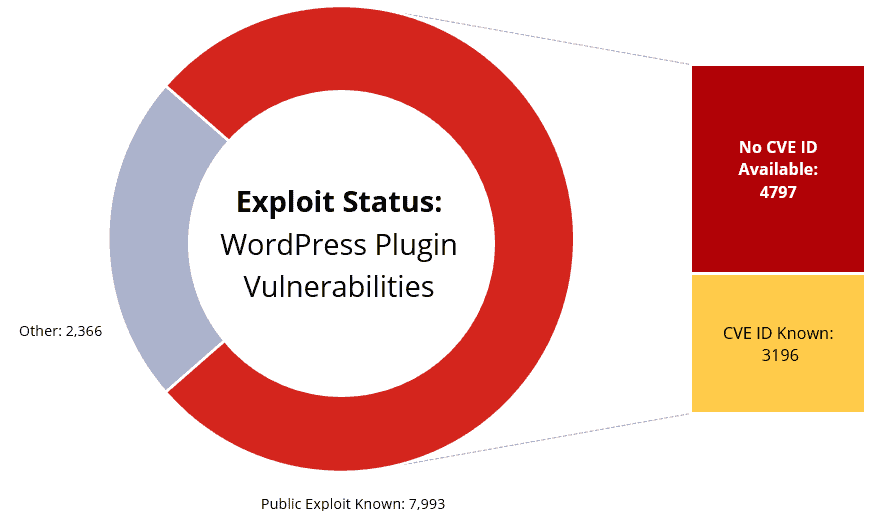
In 77 percent of the cases, the vulnerabilities are known. Therefore, it’s safe to say that providers are considerably behind in patching plugins.
7,592 of the cases concern exploits that can be activated remotely. Another 4,797 exploits are public exploits that do not have CVE code. This has significant implications for companies that only rely on the CVE standard when patching to fix problems. They are missing about 60 percent of all exploits.
Change patch policy
In addition, the researchers find that many companies base their policies on mass patching of critical vulnerabilities rather than exploitability. When a CVE or CVSS code assigns a critical rating to a vulnerability, it is often quickly adopted. However, vulnerabilities in WordPress plugins often have an average score, possibly delaying the adoption of patches. Vulnerabilities with average scores can be just as feasible.
The researchers urge companies to change their patch policy and pay more attention to the feasibility of found vulnerabilities instead of exclusively relying on ratings.