Rapid7 researchers discovered a critical vulnerability in various Zyxel firewalls. The vulnerability allows hackers to breach firewalls by remotely executing a command injection via the firewalls’ management interface.
According to the security specialist, the vulnerability (CVE-2022-30525) is relatively easy to exploit. Hackers can perform a command injection via the HTTP interface of the affected firewalls. The commands are executed as the ‘nobody’ user. An attack uses the firewalls’ /ztp/cgi-bin/handler URI.
The ease with which the vulnerability can be exploited is due to the fact that no authentication is required. The vulnerability is present in default device configurations. Resultingly, tens of thousands of devices can be remotely breached worldwide.
Multiple appliances affected
Rapid7 found that several Zyxel devices are affected by the vulnerability, as shown in the overview below.
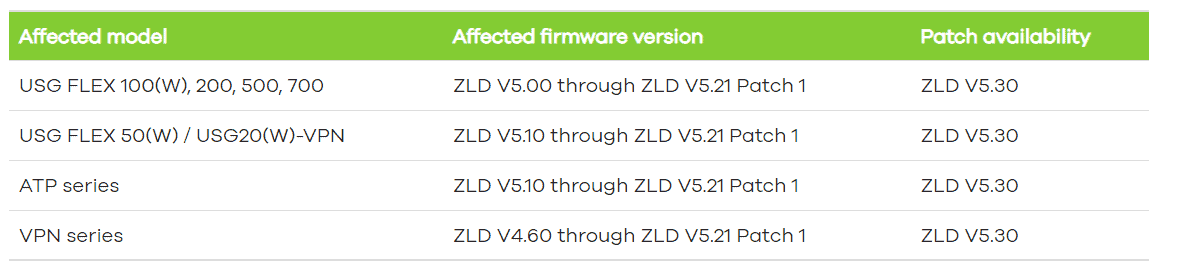
These devices have so-called zero-touch provisioning functionality (ZTP). This functionality is exploited by the vulnerability found. The affected devices are particularly suitable for smaller companies and head offices. They offer VPN connectivity, SSL inspection, web filtering, intrusion protection and email security. The firewalls can process up to 5 Gbps of data traffic.
Firmware update fixes problem
Zyxel quietly rolled out a firmware update that resolves the vulnerability. Users of the affected models are urged to install the firmware update as soon as possible.
Tip: Backdoor account discovered in vulnerable Zyxel devices
