Security researchers from NCC Group discovered a relay attack method for accessing Bluetooth devices. Some car models are affected.
The newly discovered relay attack allows hackers to access Bluetooth devices such as cars with wireless locks. These locks are typically opened with mobile devices. Attackers don’t have to be anywhere close to the authentication device. Laptops, mobile phones, smart home locks and access controls for smart buildings are vulnerable as well.
BLE vulnerability
The relay attack on the authenticating Bluetooth device uses a vulnerability in the Bluetooth Low Energy (BLE) standard. Though the vulnerability has been known for some time, existing security mechanisms can be bypassed with the newly discovered method.
The so-called link layer relay attack defeats existing applications for BLE-based proximity authentication. The research shows that there are many vulnerable BLE proximity authentication functions used in critical applications like car locks.
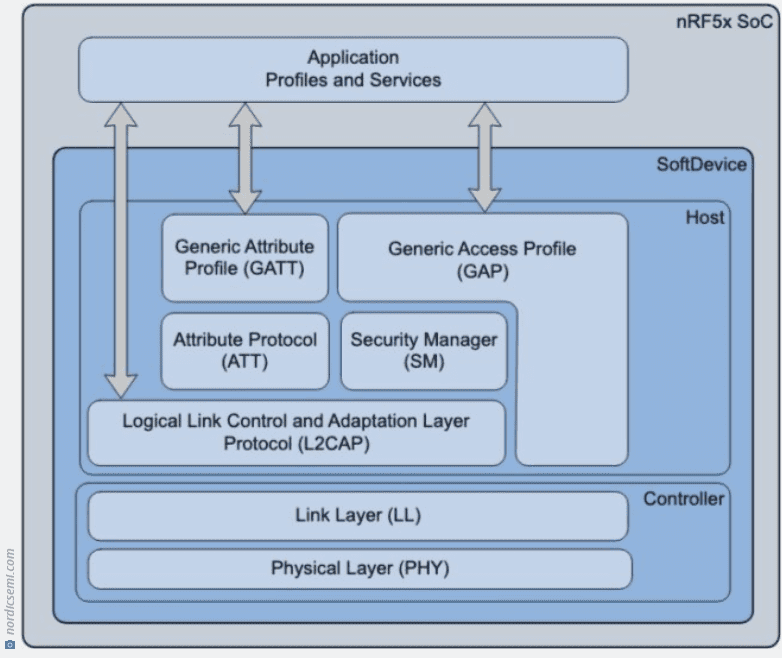
The attack on the link layer focuses on the baseband, which is where device radio signals are sent and received. This is the bottom layer of Bluetooth’s stack, purposed for announcing, creating, maintaining and closing connections. Other BLE attacks focus on the Generic Attribute Profile (GATT) layer instead, which is much higher up in the Bluetooth software stack.
Bypassing encryption
By specifically attacking the link layer, measures preventing GATT relay attacks are circumvented. There’s also less latency for data transmission, as GATT relays must pass through certain layers higher up in the stack, which acts as a bandwidth bottleneck. Link layer relays are indistinguishable from legitimate signals and can therefore be hijacked more easily.
Resultingly, authentication signals can be intercepted from a large distance and easily forwarded to a device that can eventually open the Bluetooth lock. In a restaurant, the relay device could simply hang on a coat rack, capture the credentials of a Tesla owner entering the premise and send the credentials to an accomplice waiting in the car park. The attacker can unlock the Tesla without any problems.
Possible solutions
NCC Group’s researchers advised manufacturers on ways to solve the vulnerability. Turning off proximity key functionality after a certain period of time should do the trick. Two-factor authentication fixes the issue as well. Lastly, manufacturers could disallow passive decryption and block Bluetooth on devices when the technology is not needed.
