Kaspersky researchers discovered a new malware variant that attacks Microsoft Exchange servers. ‘SessionManager’ installs a backdoor on affected systems. According to the researchers, mitigation is a difficult process.
Kaspersky notes that SessionManager has been active for 15 months. Some 34 servers from 24 companies were infected from March 2021 onwards. Around 20 of these servers are yet to be cleaned. The security experts suspect criminal group Celesium to be behind the attack.
SessionManager malware
SessionManager pretends to be a legitimate module for Internet Information Services (IIS), the standard web server installed on MS Exchange systems. IIS allows companies to streamline web infrastructure processes.
The malware deploys a powerful, near-invisible backdoor on affected servers. This backdoor allows the servers to respond to malicious HTTP requests. Hackers can use affected servers for botnets and DDoS attacks. The backdoor’s disguise makes it near impossible to detect.
SessionManager was first released in March 2021. Meanwhile, several variants have surfaced. With each variant comes new functionality. The most recent version is detailed below.
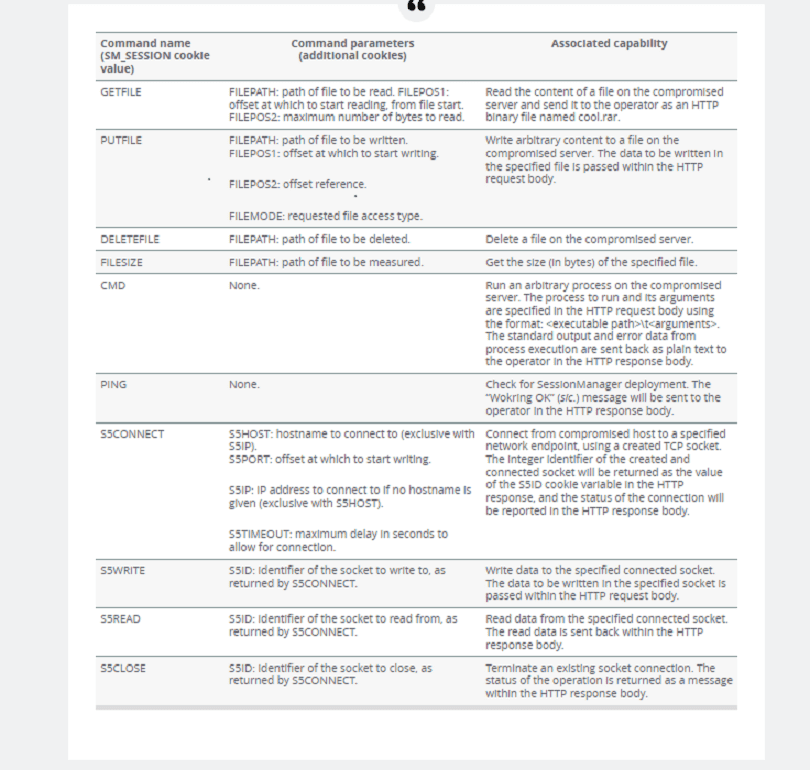
Complicated mitigation
According to Kaspersky, mitigating SessionManager is a complicated process. They urge IIS server admins to test their systems thoroughly. If the malware surfaces, teams can implement a five-step cleaning process.
Tip: Security industry is fundamentally broken: base investments on hard evidence
