Ransomware groups ALPHV/BlackCat, LockBit and Karakurt adopted a new way of extorting victims. The data of breached companies are searchable on leak websites.
Ransomware groups frequently implement new blackmailing methods. ALPHV/BlackCat, LockBit and Karakurt recently started allowing website visitors to query databases of breached info. This allows anyone to systematically search for victims and data. The groups hope to pressure victims into paying.
Search engines
ALPHV/BlackCat developed a proprietary search engine. Victims are told their data is indexed. Queries aren’t the most accurate, but effective at increasing pressure nonetheless.
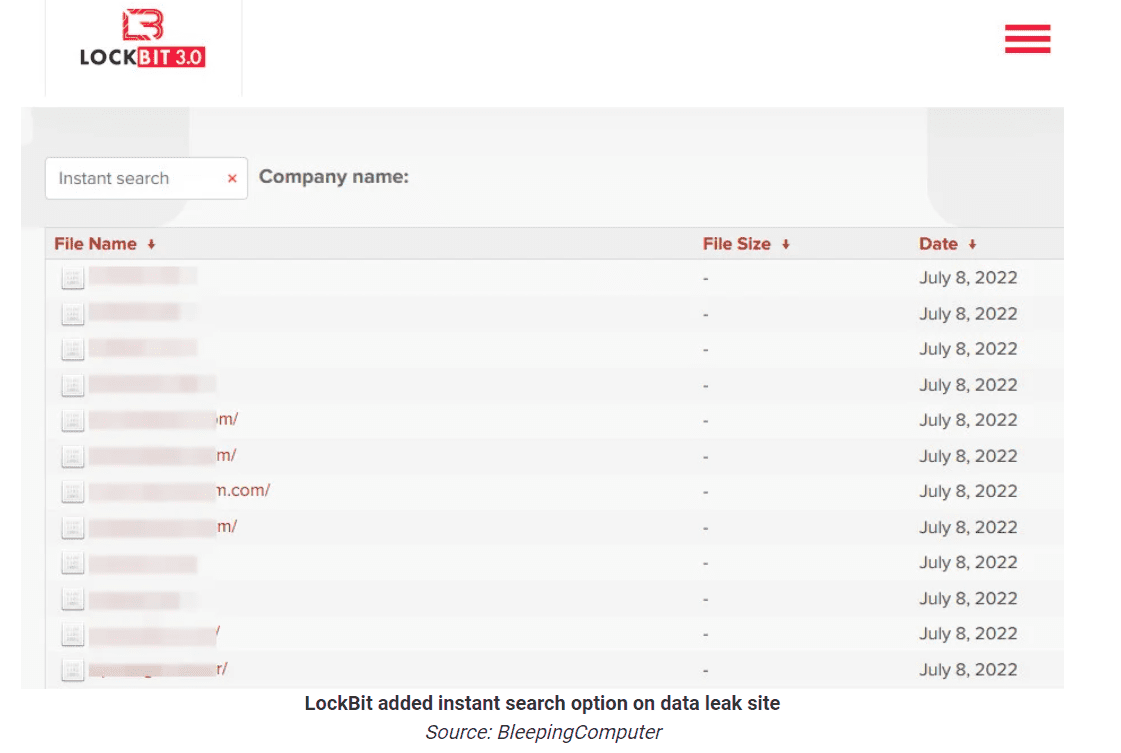
LockBit developed a search engine as well. The tool is available on the group’s latest leak website. Parameters are limited to the names of victim companies. In contrast, the search engine of ALPHV/BlackCat allows users to dive into multiple keywords.
Karakurt is also working on a search engine. Unlike the tools mentioned above, this project is still in its infancy. The engine fails to produce relevant results at the time of writing.
Ransomware groups are entering a new phase. It’s been clear that top groups operate like software companies for some time. Research by Group-IB tells us that ransomware groups actively invest in R&D. Database technology is one of the results.