Palo Alto Networks warns of a major vulnerability in its PAN-OS operating system. The OS is included in the security provider’s solutions.
Palo Alto Networks indicates that the vulnerability (CVE-2022-0028) is actively exploited and highly sensitive. The bug allows unauthenticated hackers to perform amplified remote TCP DDoS attacks. The vulnerability originates from a URL filtering policy misconfiguration.
The misconfiguration allows hackers to exploit devices based on the PAN-OS operating system for DDoS attacks. In doing so, the original IP address of the hackers is hidden, which makes troubleshooting difficult.
Palo Alto Networks discovered the vulnerability after the security provider became aware that a security device had been used in a reflected DoS attack. Further analysis indicated that the vulnerability is actively abused.
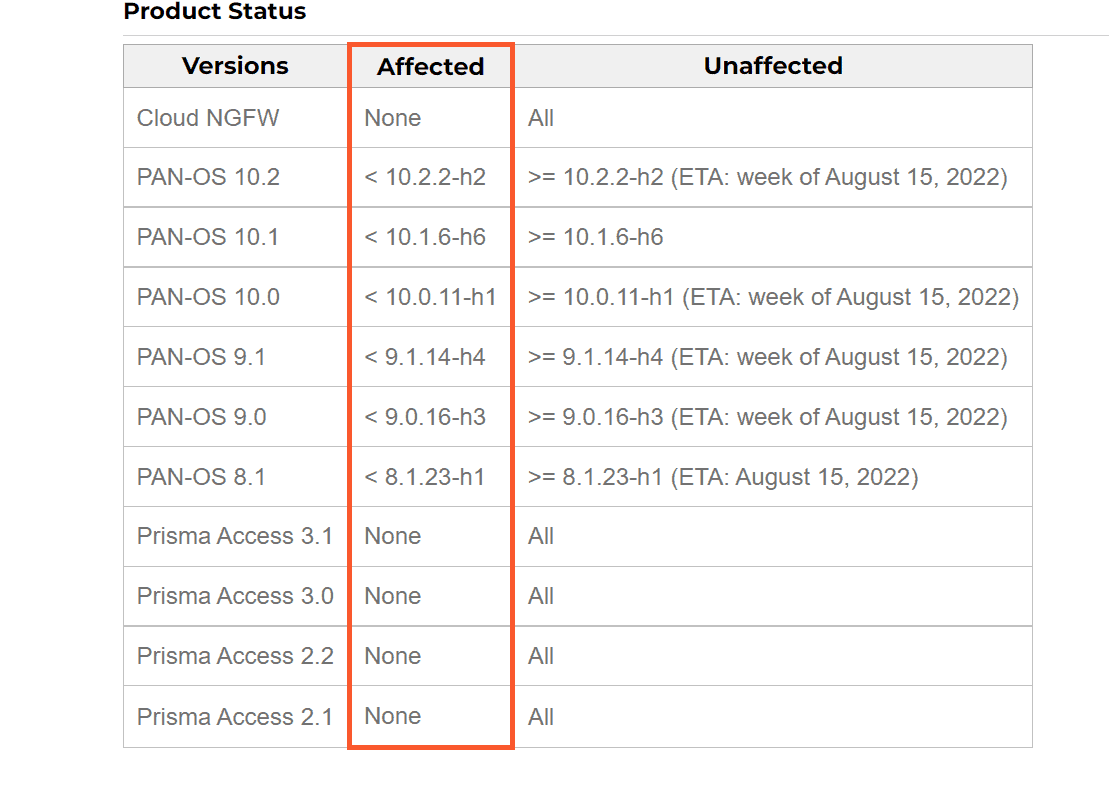
Present in multiple OS versions
The vulnerability is present in several versions of the operating system. A patch is now available for versions earlier than 10.1.6-h6. The patches for versions 10.2.2-h2, 10.0.11-h1, 9.1.14-h4, 9.0.16-h3 and 8.1.23-h1 will become available next week.
Conditions for vulnerable devices
Furthermore, the vulnerability only lies in PAN-OS versions running on Palo Alto’s PA, VM and CN security device series. Devices must meet three additional conditions in order to be exploited.
First, the security policy on the firewall must allow traffic from Zone A to Zone B and have a URL filtering profile with one or more blocked categories. Second, packet-based attack protection functionality must be unchecked in a Zone Protection profile.
The third and final condition is that ‘flood protection via SYN cookies’ is disabled in a Zone Protection profile for Zone A with an activation density of 0 connections.