Shikitega, a newly discovered Linux malware variant, installs a persistent cryptominer and makes itself invisible through a so-called polymorphic encoder.
AT&T researchers unveiled the malware variant in a recent report. Shikitega targets Linux computers and IoT devices. Cryptominer payloads are gradually deployed on vulnerable devices.
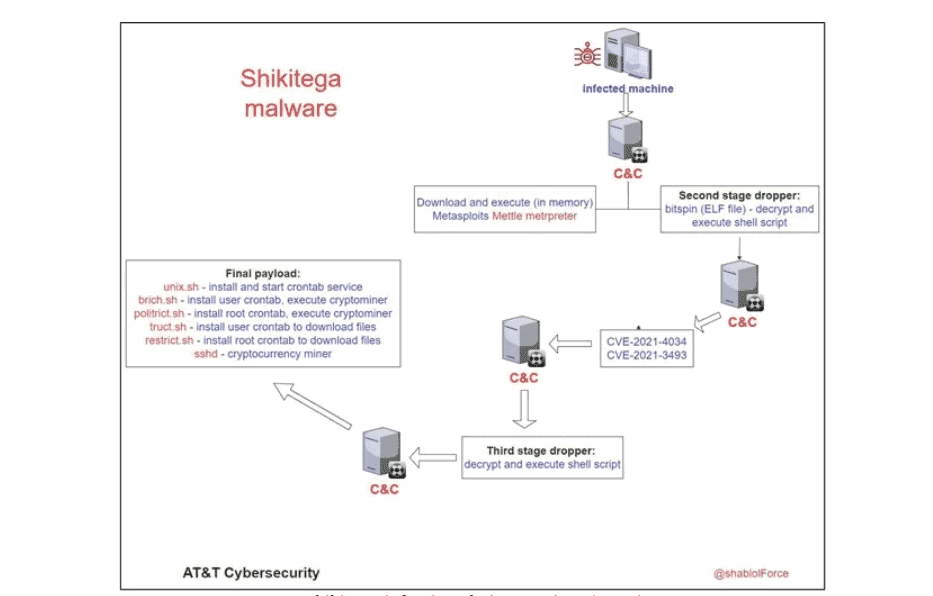
Infection process
Shikitega’s anti-detection measures are remarkable. A polymorphic encoder blocks static signature-based detection. The malware uses a multi-step infection process, with each step delivering a snippet of malicious code. Each snippet consists of several hundred bytes. The snippets eventually combine to activate a simple module, which proceeds to active the next.
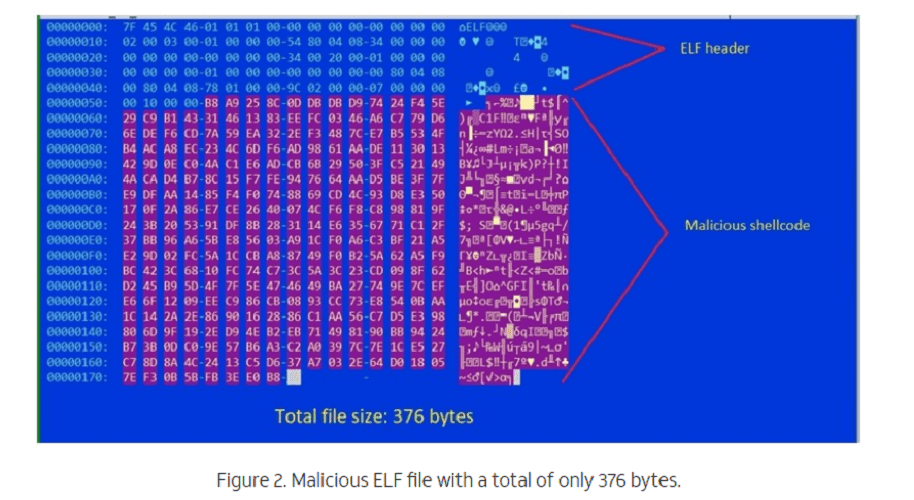
The process starts with a 370 kilobyte ELF dropper containing the shellcode. Encoding is performed by ‘Shikata Ga Nai’, a polymorphic XOR encoder. The encoder was previously discovered by security experts from Mandiant.
The malware runs through several decoding loops, each loop decoding the next layer. This process continues until the final shellcode is decoded and executed. The so-called ‘encoder stud’ is generated based on ‘dynamic instruction substitution’ and ‘dynamic block ordering’. The registers are also selected dynamically.
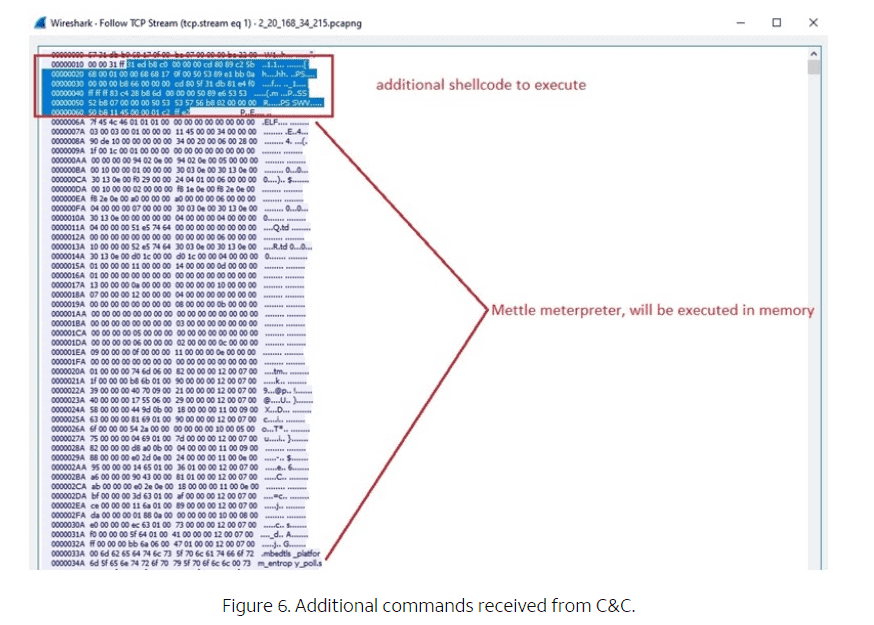
When executed, the shellcode contacts the attackers’ command and control servers. Finally, the affected device receives additional shellcode commands that are stored and executed within its memory.
Installing the cryptominer
One of the commands downloads and activates ‘Mettle’, a small and portable Metasploit Meterpreter payload. The payload provides attackers with remote control and code execution options. Mettle installs a cryptominer (XMRig 6.17.0) and ensures that access privileges are granted. XMRig 6.17.0 is capable of stealthily mining cryptocurrency like Monero.
Persistence and detection
The cryptominer manages to remain on the host through five downloaded shell scripts. Among other things, the shell scripts install crontabs for the root user and current user. The cronjobs wipe previously installed files to thwart detection. According to AT&T, attackers typically use legitimate cloud platforms to further hide their actions.
