
Wiz sees big impact of AI on runtime security, but also stresses old threats
Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...

Cloud security has evolved beyond a specialized domain to encompass virtually all aspects of modern cybersecu...
Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Password manager LastPass is under fire. In recent days, hackers made several attempts to break into the pass...

Another vulnerability was discovered in Log4j. Accordingly, the Apache Foundation released a patch. Version L...

Security will continue to be one of the most important concerns for companies in 2022. According to Neustar I...

The Biden administration is investing in open-source software security. Bloomberg reports that several open-s...

Security specialist Snyk is considering going public next year, Bloomberg reports. The IPO should generate mo...

Security specialist Wiz warns of a vulnerability in Microsoft's Azure App Service. Abusing the vulnerability ...
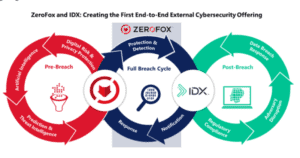
ZeroFox, a cybersecurity firm, is set to go public via a special-purpose acquisition company merger with L&am...

The agency donated the passwords to an anti-hacking public service site This week, Britain's National Crim...

BlackBerry releases a major update of its MDR service. Guard 2.0 offers XDR functionality. The service is bas...

VMware is warning customers about a vulnerability in its Verify two-factor authentication solution. Hackers a...