
Security

Cybersecurity has been a challenge from the beginning of IT and it will be until the end. It all started with endpoint and network security, but today we are also dealing with cloud security and training our employees to incorporate good security practices. All these new technologies that help us innovate also help cybercriminals and state-sponsored hackers get new tools that they can use to access our systems and, in the worst cases, gain access to our most valuable data and trade secrets. Moreover, with new legislation such as GDPR, you have to make sure everything is secure or you will not only lose your reputation, but you could also be fined by the government. In short, protecting IT environments is more important than ever.
Timeline

AWS and SentinelOne offer Purple AI on Amazon Bedrock
Expanding SentinelOne's partnership with Amazon Web Services (AWS) allows customers to choose which LLMs with...

Even security experts have poor password hygiene
As many as 68 percent of the IT and security managers reuse system passwords. This is according to researc...

HashiCorp’s security tools Vault and Boundary get important new features
In addition to improving its infrastructure offerings, Hashicorp is also updating the other part of its produ...

Oktane 2024: agents, security and the fight against SaaS chaos
Okta has had it with the "mismash" of identity security solutions

SentinelOne wants to make the autonomous SOC a reality
More autonomy, less burden on employees

Cisco investigates possible data breach after IntelBroker attack
Cisco is investigating claims that hackers led by IntelBroker caused a data breach at the company. Meanwhile,...

Cybercrime victims suffer £808 loss and mental trauma to boot
Research once again reveals the true damage of cybercrime. Individuals who have been deceived by an attacker ...

Cognizant and Palo Alto Networks partner on security services
Cognizant and Palo Alto Networks announce a strategic partnership to deliver AI-driven cybersecurity solution...
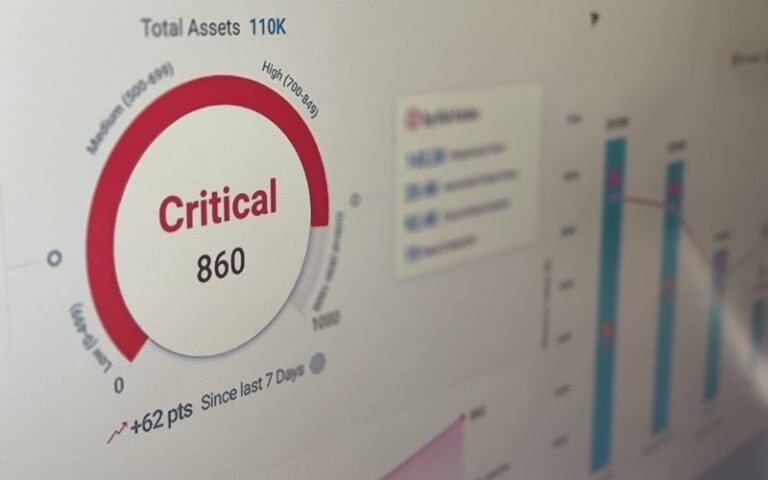
Qualys QSC: Sealing the lid on container security
Cloud computing security and compliance specialist Qualys held the main Americas leg of its annual multiple-l...
