
Apple Vision Pro: will it shake up the way we work?
It's been confirmed: Apple will be releasing a headset that it has called Apple Vision Pro. For the first tim...

It's been confirmed: Apple will be releasing a headset that it has called Apple Vision Pro. For the first tim...

Oracle has multiple large AI projects. The company finds generative AI appealing as well. Yet Oracle does not...

Databases move. By their nature, developers and database administrators (DBAs) along with the full cadre of O...

Managing a complex multi-cloud environment is no easy task. Emma's multi-cloud platform wants to make clouds ...

Data centers are only becoming more important. The rise of the digital medium in enterprise means that organi...

Wasm is what’s up. In terms of the hot technologies discussed at any of the major enterprise IT shows being...

Reports about the potential dangers of AI are coming thick and fast. We often hear these voices emanating fro...
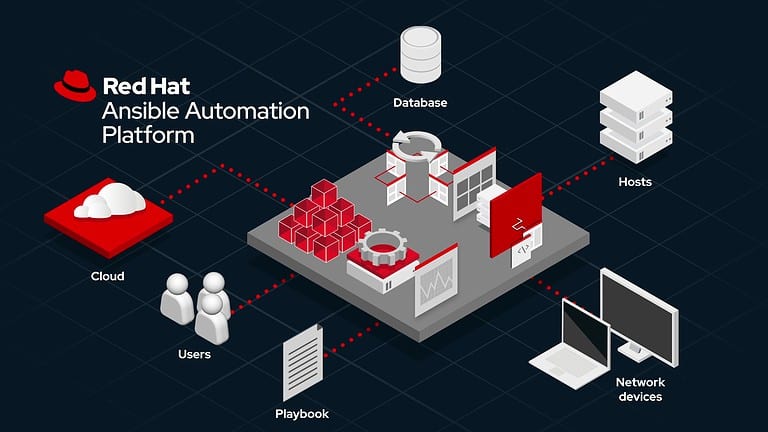
Red Hat presented some much-needed innovation for Ansible at its summit in Boston. One very big change is tha...
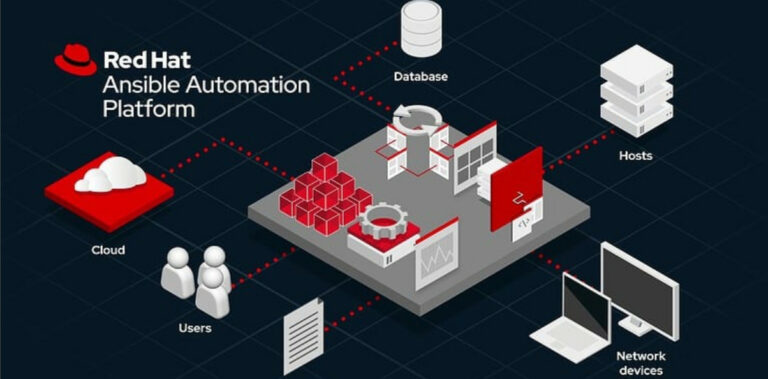
Red Hat presented some much-needed innovation for Ansible at its summit in Boston. One very big change is tha...
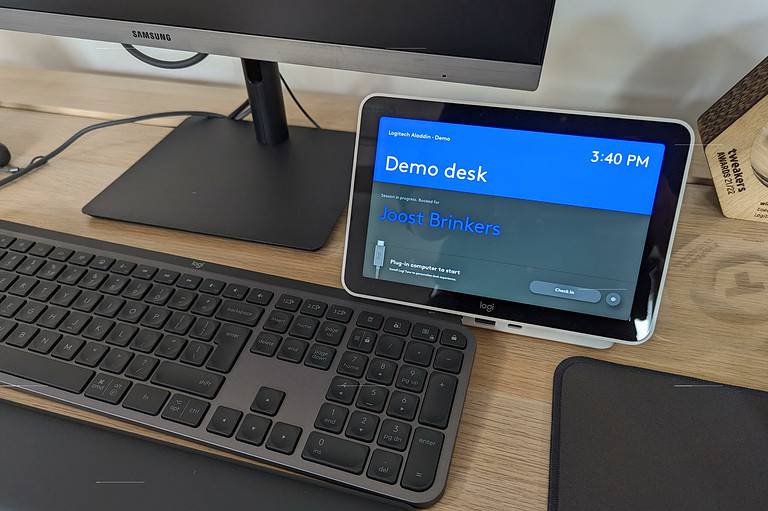
A conferencing camera, a laptop dock and a flex workspace management solution: the connection between Logitec...