Sysdig has just released its annual Global Cloud Threat Report. Because of the complexity of cloud environments, hackers can often be difficult to detect while having an attack in place within 10 minutes of discovering credentials.
The Sysdig team warns that a recon alert is the last chance for security engineers to nip an attack in the bud, while a discovery alert is already a sign that one is too late. Once an attacker is in, the dwell time on-prem is an average of 16 days – Sysdig cites research by Mandiant for this metric.
Why specifically telcos?
One notable finding from the Sysdig team is that cloud attacks target telecommunications companies 38 percent of the time. Financial institutions are a close second at 27 percent, while it also surprised the researchers that healthcare (5 percent) and defense (1 percent) aren’t targeted by a cloud attack nearly as often.
Sysdig suggests that more sophisticated attackers may not be scanning for public cloud buckets, but are proceeding more precisely. In addition, according to the researchers, it is possible that cloud hackers are primarily concerned with stealing, say, bank data for $35 per victim.
What are attackers looking for?
The research shows that attackers are mostly looking for serverless function code and Infrastructure-as-a-Service software (such as CloudFormation and Terraform). This is because these often contain login credentials or other sensitive information.
The collection method is predominantly automated, but there is a human in real-time waiting for the information. Hence, according to Sysdig, targeted cloud attacks can occur within 10 minutes.
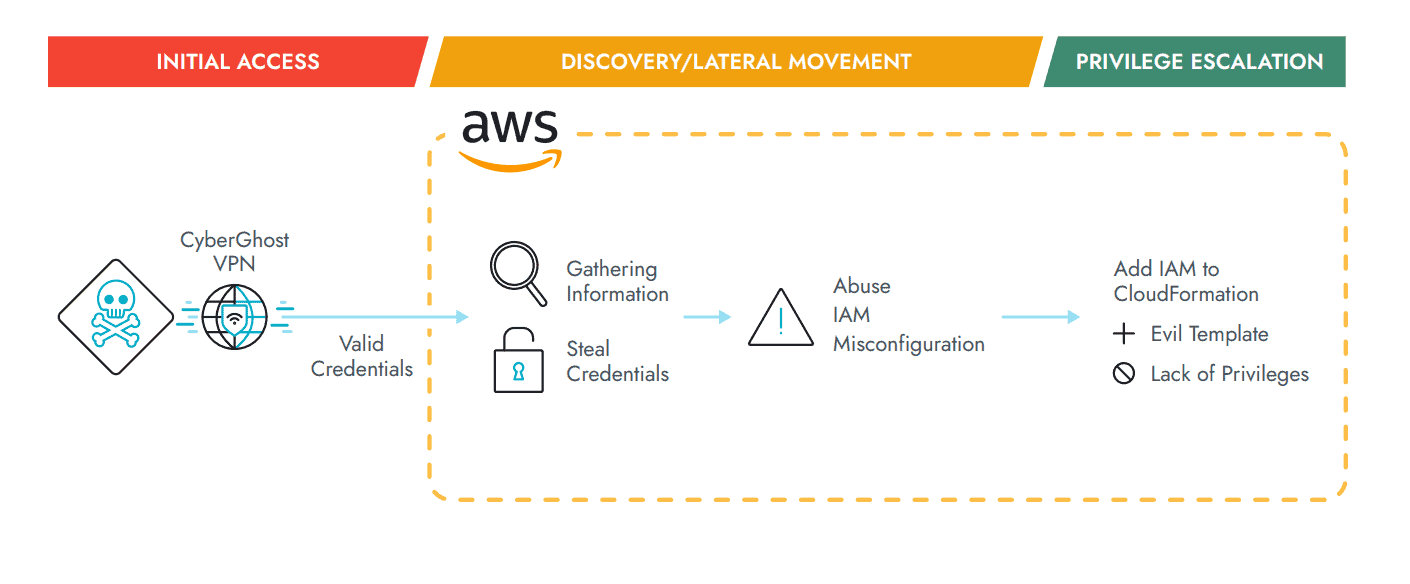
A well-known step after initial access is for hackers to try to escalate their privileges. Errors in the setup of cloud environments can be enough for this: for example, an admin account that does not comply with the general naming structure can already lead to a further step in a hacker’s attack strategy.
Unseen
The revenue model of these malicious actors varies, but crypto-mining is and will remain a lucrative opportunity. For organizations that do not accurately track all hardware resources, it can go unseen for a long time. It then costs organizations $53 in energy consumption for every $1 the attacker earns through the illegal practice. Another example is proxy jacking, where stolen IP addresses are resold to proxy services.
Tip: New cybercrime tactic: selling someone else’s Internet connection
Attackers can use an AWS VPC (virtual private cloud) to spoof their IP addresses. By doing so, they not only hide their own identity but also appear unsuspicious in a cloud environment.
Attackers are quite sophisticated in terms of information gathering. They track changes to victim accounts to take advantage of them – even a small error can lead to the theft of credentials. Sysdig states that such attacks are not very subtle, however: the “telltale signs” are that there are numerous queries at endpoints that can be picked up in data logs.
Solutions
The Sysdig researchers advise those looking to set up better cloud security to set up a secrets management system alliteratively. They explain that a central location is reserved for keys and credentials that can be accessed via an API. This prevents an organization from having a key sitting somewhere among corporate data.
In addition, Sysdig recommends a good CSPM solution. These provide options for visibility and incident resolution to secure cloud accounts better.
Runtime threat detection can also provide better protection, according to the researchers. These should be applied to cloud logs and activity in computing resources to get a complete picture of a cloud environment. Here, it is important to include visibility into multi-cloud environments, which is precisely where many problems can occur. It is therefore crucial to have a good overview of all cloud assets.