SentinelOne recently uncovered a vulnerability in HP and Samsung printers. This is a so-called escalation of privilege vulnerability that originated in a poorly designed and not properly maintained printer driver. CVE-2021-3438, as the vulnerability is officially called, has received a CVSS score of 8.8 (out of 10).
When you install a printer or multifunctional you usually launch a piece of installation software. With this software you can set everything up for first use. For example an SMTP-server for sending scans through the mail, but also the admin-password.
An important part of the installation of a printer is the installation of the driver on a PC. After all, without a driver, a printer will not work. During the installation of a printer you will not generally see a question whether or not you wish to install the driver, apart from instances in which you can select from various different types of driver. Installing a driver is implicit in putting it to use, so that makes sense. In other words, you’re not going to answer “No” to the question of whether you want to install the driver.
Vulnerable driver
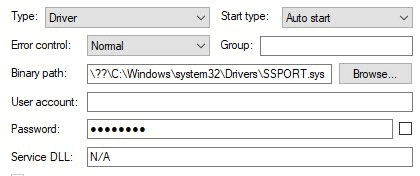
If, however, something is wrong with that driver, then you do install a vulnerability on your machine without even noticing it. The latter is what has happened to millions of HP and Samsung printers and multifunctionals, but also to several Xerox devices, since 2005 according to reports. For 16 years, the installer of these printers has been installing the (old) SSPORT.SYS driver. More than 380 different models are affected. You can find the entire list from HP and Samsung here. At Xerox, the list is significantly shorter. They are exclusively laser printers, as far as we can tell.
At first glance, the SSPORT.SYS driver seems to come from Samsung. As far as we know, SSPORT stands for Samsung Serial Port driver. However, HP only acquired Samsung in 2017, which makes 2005 a bit odd. Why would that driver have been in printers from both Samsung and HP since 2005? We know that there are only a few printer manufacturers in the world. HP buys the components for laser printers from Canon, for example, but assembles the printers themselves. Xerox does have its own or jointly owned facilities, but it also gets certain models from elsewhere, so in this case HP. If you go through the list, you do see many more Samsung models than HP models. So there is a real chance that this vulnerability was introduced with the acquisition of Samsung.
At SentinelOne, they delved a little deeper into the history of the driver. That research shows that HP/Samsung most likely didn’t even write the driver themselves, but took it from a Microsoft project in Windows Driver Samples. However, where Microsoft’s project removed all vulnerabilities from the driver, HP/Samsung’s implementation was rather sloppy.
What exactly is going on with this driver?
Everyone who has a printer from the list we link to above has this driver on their machine. So that makes it a very critical vulnerability. Note that even if you have installed a printer from that list and it is not (anymore) in use or you have aborted the installation, this driver most likely is still on your system. On top of that, the driver is also always auto starts when you turn on your machine.
A driver like SSPORT.SYS is, in theory at least, a target that makes attackers very happy. After all, it’s on PCs without anyone noticing, and it’s also always active, regardless of whether a printer is connected or not.
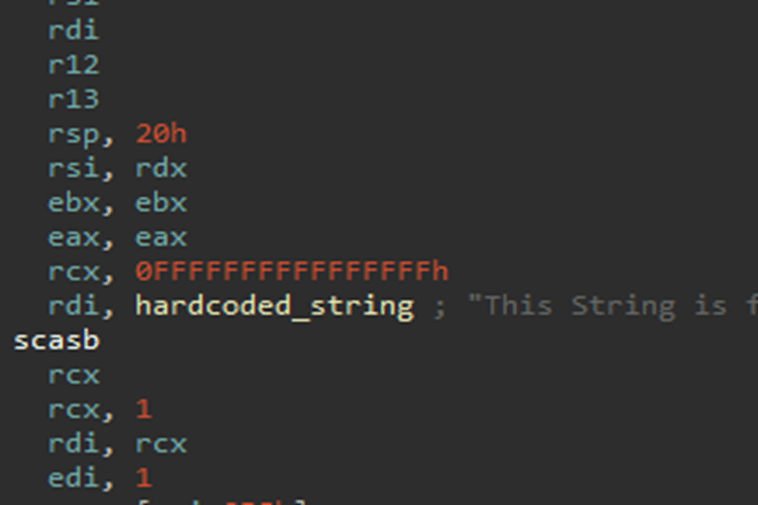
Just having a driver that’s always running isn’t enough to call it a vulnerability, though. However, there is also something not quite right with the driver. It is possible to send so much input to the driver from User Mode (via Input/Output Control, or IOCTL) that the driver’s buffer overflows. This enables attackers to get into the actual system and thus run code in Kernel Mode. Once there, for example, code can be made active that bypasses the security of a system. To stay in the terms of the security world, we are dealing with an escalation of privilege here.
All this is not so easy to weaponize, if we read SentinelOne’s findings. In any case, the vulnerability alone was not enough to cause any harm. So there is a chance that other vulnerabilities and bugs will have to be used for that. Or an attacker may have to spend more time to weaponize it than the folks at SentinelOne did. At the moment there are no indications that attackers are actively using this vulnerability and/or knew about the existence of the vulnerability.
HP acts fast, provides patch
As they should, HP (and Xerox) have gone to work and you can download and install the patch for this vulnerability on the pages we also linked to above. For the sake of completeness you have them here again: HP, Xerox. According to SentinelOne, HP also acted in an exemplary manner after SentinelOne reported the vulnerability and quickly came up with a patch. Still, given the strong focus on security of their printers, it will sting HP Inc. quite a bit that this has come to light. If it’s true that this driver was more or less copied and pasted from a Microsoft project and not looked after, it’s pretty sloppy.
Security companies like SentinelOne typically spend a fair amount of time testing all sorts of pieces of software on systems to make sure they are secure enough. This story is one example, but a few months ago we also reported on a 12-year-old vulnerability in Windows Defender that was discovered by SentinelOne.