Microsoft is aiming to improve the availability and uptime of Azure Active Directory (ADD). For this purpose, it has launched a backup authentication service. The service will soon allow ADD customers to use an ‘outage mode’ in case of downtime.
Downtime of Microsoft’s Azure Active Directory (AAD) has major consequences for companies that are heavily dependent on Microsoft’s cloud services. After all, AAD handles all user authentication for access to Office 365. Other applications can also use AAD, which means that problems are often incalculable in the event of an outage.
Backup authentication service
Microsoft is well aware of this, as exemplified by recent projects to improve ADD’s availability. Since the end of last year, uptime rose to 99.99 percent. To further enhance the latter, the tech giant announced a backup authentication service.
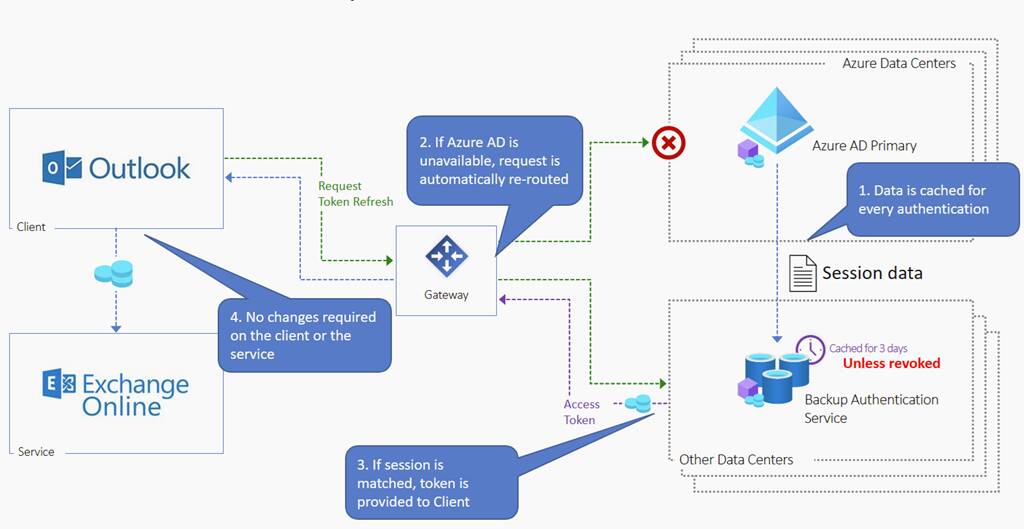
The backup authentication service replicates and stores the various authentication data during AAD’s regular working hours. When AAD suffers a disruption, it goes into a so-called outage mode. Using the previously replicated authentication data, AAD can still check requests and issue user authentication tokens.
This ‘outage mode’ for AAD now includes authentication for both web and desktop applications. Initially, the service was only available for Outlook Online and SharePoint Online. Now, the tech giant announces that the service will become available for environments running Active Directory on-premises.
In addition to web and desktop applications, mobile applications are covered. Shortly, the ‘outage mode’ will be extended to Teams Online and the rest of Office 365. Dedicated applications based on Open ID Connect are to follow soon.
Discussion of quality
The backup authentication service for AAD promises a lot, but whether we’re actually dealing with a quality solution is still up for debate. Experts indicate that outages of Outlook and SharePoint at the end of last year did not immediately lead to a quick recovery using the service.
The service can only handle a limited number of authentication credentials. Microsoft assumes that Office 365 users seek access daily and from a single, consistent device. For this, the service only stores authentication data from the past three days. However, if users try to access with a new device, they are not allowed access, as the authentication data for the new device does not correspond to that of three days earlier.