Log-in data of victims of phishing attacks were available on various hacked WordPress websites. These websites, and therefore the stolen login data, were indexed by Google.
Check Point Research writes about the findings in a blog post. The attackers first managed to hack existing WordPress websites and used their domain to send phishing emails. Because antivirus programmes trusted the existing websites, they did not end up in the spam box.
Scans from Xerox
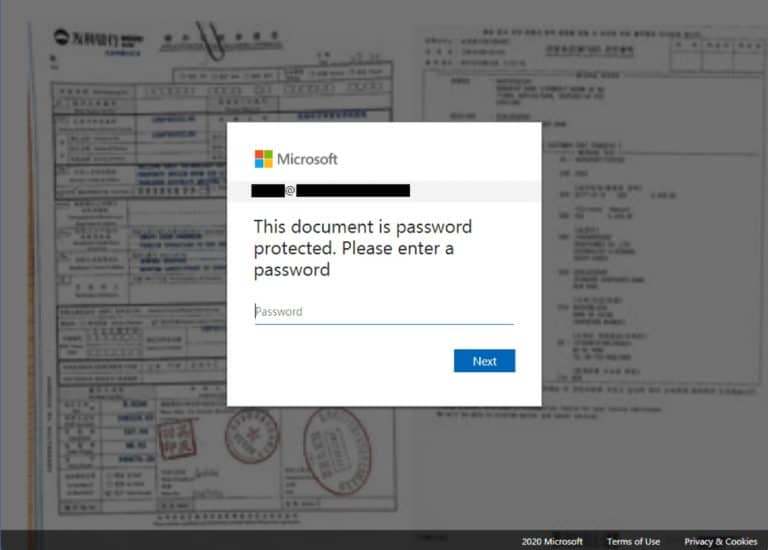
The emails appeared to be sent by Xerox as if they were sent from a printer. They were accompanied by a simple text notifying the victim that a scanned document was waiting for them. The attachment contained an HTML file that directed the user to a web page. Once on the web page, the user was presented with a blurred image and a pop-up to message that the document was protected.
Microsoft 365 login
To view the document, users had to log in with their Microsoft 365 account. The password the user entered was then forwarded to a legitimate Microsoft server to verify it was correct. The attackers then redirected the victim to a genuine Microsoft login page. In this way the attackers were able to avoid detection by Microsoft Advanced Threat Protection.
Indexed by Google
The stolen passwords were then stored on the hacked WordPress sites. However, the way in which these were stored was public in nature and the websites were indexed by Google, so the stolen data could be found via Google.
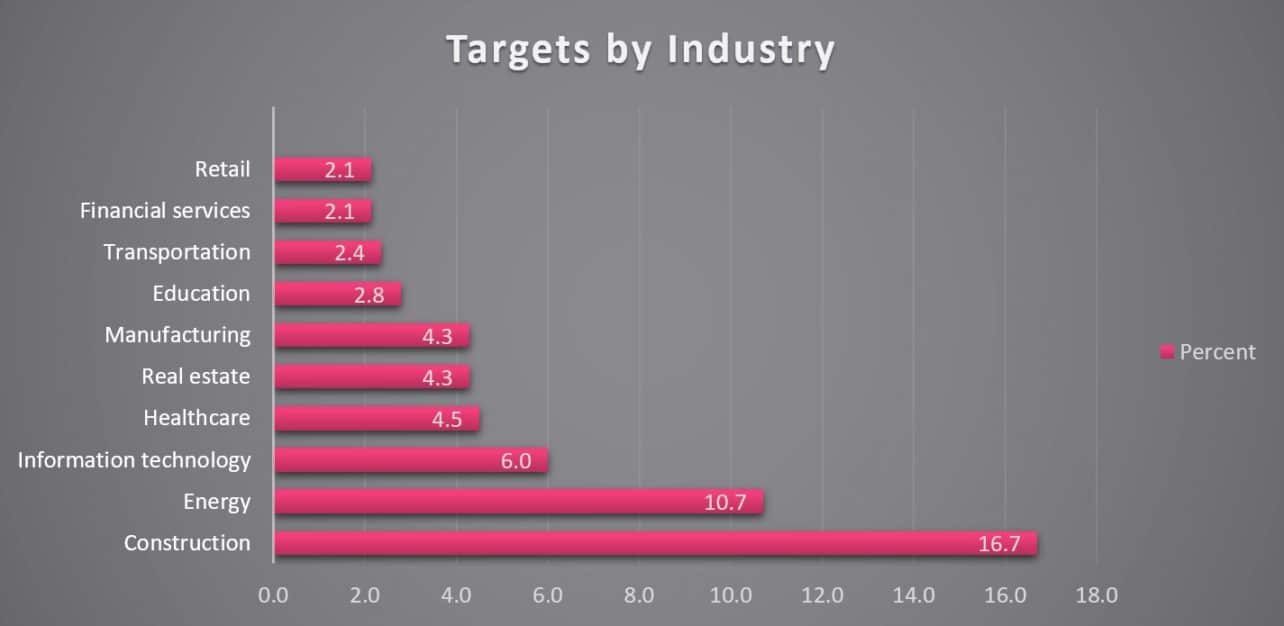
Construction industry
Based on the stolen data, the researchers were able to form a picture of victums the attackers were aiming at. The stolen passwords appeared to belong mainly to employees in the construction and energy industries.
Check Point has informed Google about the indexed web pages.
Tip: Admins will now be able to run phishing simulations on Office 365