Security specialist ProofPoint has recently discovered active malware called CopperStealer, which actively targets the theft of passwords and other login data for major tech platforms. In collaboration with Facebook, Cloudflare and others, the malware was defused.
The CopperStealer malware was spotted at the beginning of January this year, and Proofpoint immediately started an investigation. The security specialist discovered that this malware was aimed at stealing passwords and other login data from major tech platforms. Initially mainly Facebook and Instagram, but later Apple, Amazon, Bing, Google, PayPal, Tumblr and Twitter as well. The researchers see an affinity between CopperStealer and previously discovered malware families such as SilentFade, StressPaint, FacebookRobot and Scranos.
According to the researchers, CopperStealer is an annoying kind of malware. More than 80 different variants were in circulation. In total, the security specialists detected 4,655 unique attacks in 159 countries, with India, Indonesia, Brazil, Pakistan and the Philippines as the most important countries.
Stealing data from browsers
The specific aim of the attacks was to steal data from Facebook and later from other tech platforms, stored in browsers such as Chrome, Edge, Yandex, Opera and Firefox. With these credentials, the hackers then sought unauthorised access to these platforms to place malicious advertisements and earn money in this way.
The CopperStealer malware infects users of the tech platforms when they download software bundles from certain websites. These sites offer the software illegally and are advertised as so-called “KeyGen” or “Crack” sites. Samples of the software are hosted on these sites, but they often come with a lot of malware, such as CopperStealer. Providers of this software want to use this to circumvent the licence restrictions of the software.
Cookies abused as well
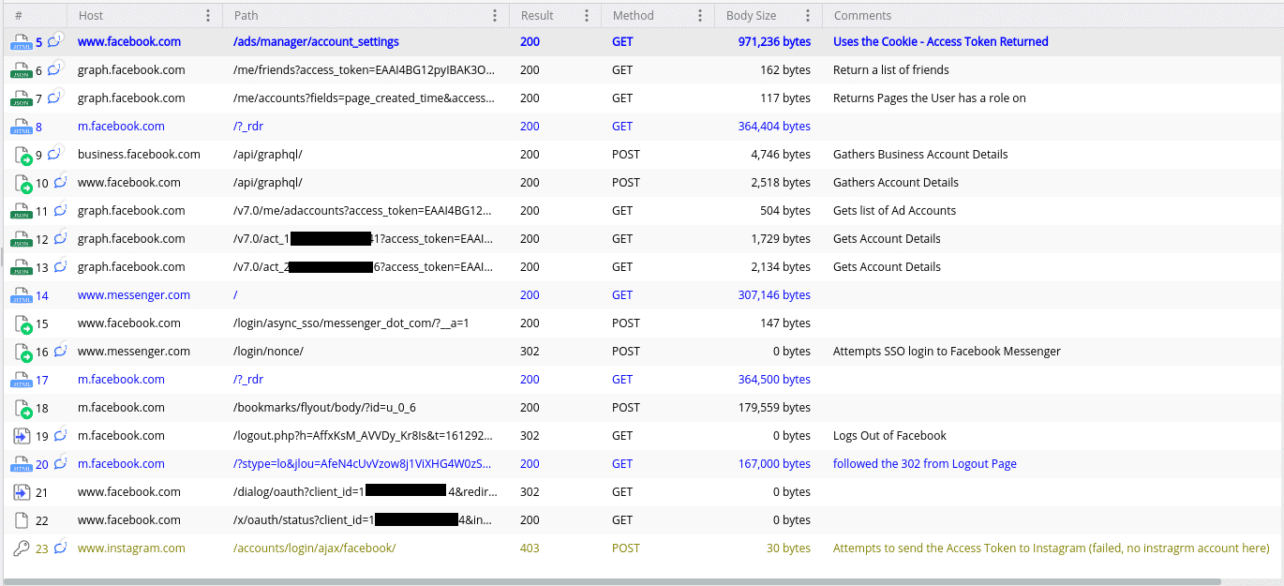
In addition to passwords, CopperStealer also stole cookies stored in the browsers, according to Proofpoint. This was done in order to retrieve a User Access Token from Facebook. With this token, the malware requested additional information from Facebook and Instagram for more context. For example, lists of friends, advertising accounts of the affected users and a list of pages to which the affected users had gained access. This of course allowed the malware to spread.
Combating CopperStealer
Proofpoint, Facebook and Cloudflare decided to disrupt the CopperStealer distribution. To do so, Cloudflare posted an alert for the malicious domains and created a so-called sinkhole for two of these domains before they could be registered by the hackers. A sinkhole limits the hackers’ ability to collect data from victims and gives security specialists time to collect data on the victims and investigate the behaviour and scope of the malware.
In the first 24 hours the sinkholes were online, 69,992 HTTP requests from 5,046 unique IP addresses from 159 countries were logged. These corresponded to 4,655 unique infections, mainly from Asia.
After 28 hours of activity of the installed sinkholes, the malware traffic decreased dramatically. Also, the malware was no longer being distributed via some of the investigated websites.
Tip: Proofpoint sues Facebook to keep using lookalike domain names
