A bug discovered in Apple’s browser, Safari, can leak users’ identity and website history. The vulnerability is related to WebKit code and was detailed on January 14th by researchers from FingerprintJS Inc.
The vulnerability comes from Safari 15’s implementation of the IndexedDB application programming interface. The browser API is intended for client-side storage and is designed to hold a significant amount of data. Many browsers use the API.
After disclosing the vulnerability to Apple and the WebKit Bug Tracker in late November, it has taken until January 17th to fix.
Where Apple dropped the ball
Even though many browsers use the IndexedDB API, the way Apple implemented it in Safari violated the ‘same-origin’ policy which prevents interaction between documents and scripts in one place with those in another.
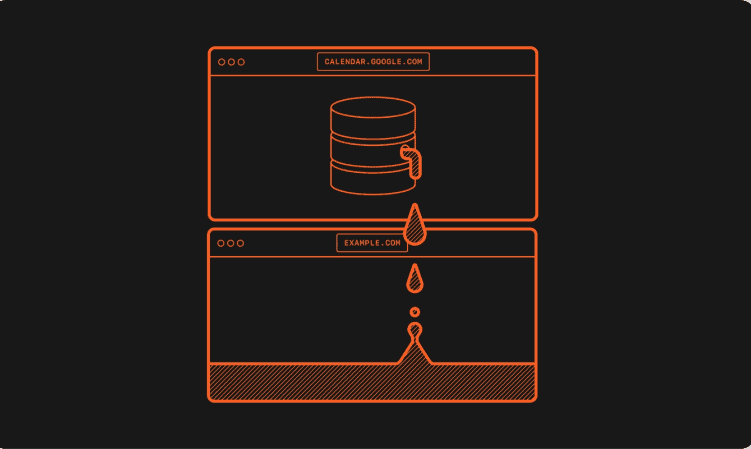
Because of that implementation choice, a malicious actor can find Google LLC account information and history from open windows and tabs. The problem does not affect the data in the IndexedDB. However, it exposes the names of the databases.
In some of the cases, the researchers discovered some websites that leverage user-specific identifiers in the database names. What that means is authenticated users can be uniquely and accurately identified.
What malicious actors want
The information the APIs expose is controlled by many factors. However, the researchers said that generally, at minimum. The user’s profile picture is usually available. Therefore, an untrusted or malicious website can find out a user’s identity and link multiple accounts used by the same person.
FingerprintJS has created a demo page you can view here, where the researchers show how the identities are leaked when they are logged into their Google account in the same browsers.
In the demo, the presence of 20 or more websites is detected running in other browser tabs or windows, including Twitter, Bloomberg, YouTube, Google Calendar, and more.