Business-grade DrayTek routers are under attack by the Hiatus malware campaign. The successfully attacked routers are transformed into “listening posts” that can intercept email and steal files.
Security experts at Lumen note that the Hiatus malware campaign has been active since July 2022. The campaign appears to target mainly DrayTek Vigor routers (the 2960 and 3900 models) based on Intel i3 architecture. These routers support employee or remote VPN connections.
In addition, pre-built binaries of the malware are also reportedly already circulating for Arm, MIPS64 big endian and MIPS32 little endian platforms.
Attack technique
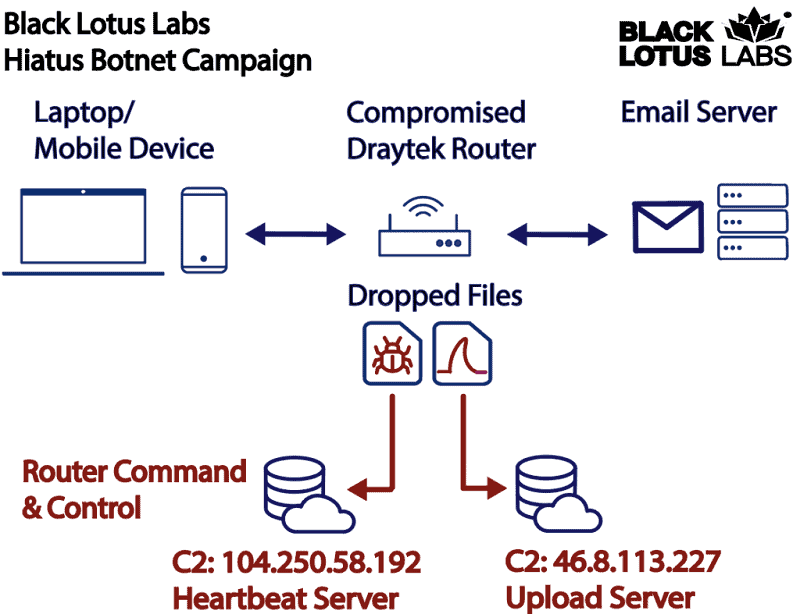
Included software would hide the source of the infection. The security experts discovered that after the hacking attempt, the Hiatus malware installs via a bash script. This malware then downloads and installs two binaries.
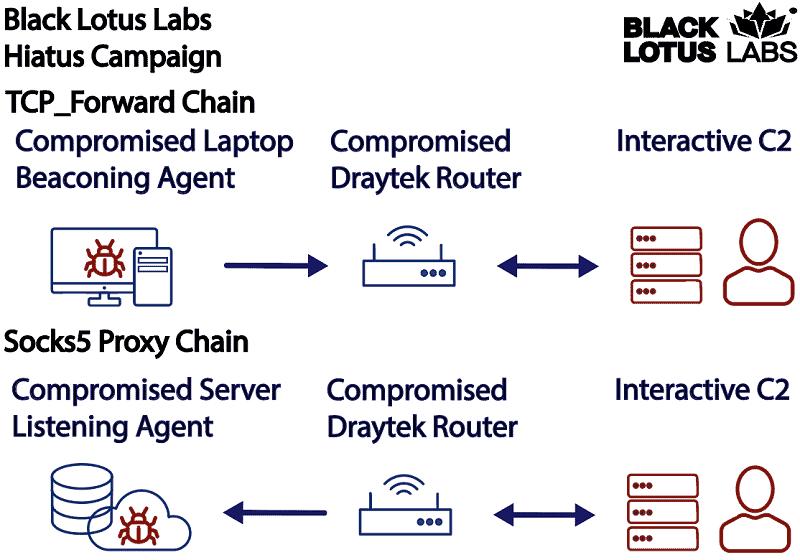
First and foremost it is HiatusRAT. This binary allows cybercriminals to execute commands or install new software on the affected device. In addition, the binaries turn the device into a hidden proxy and then becomes possible to intercept router traffic on ports used for e-mail and file-transfer communication.
The second binary installed is the HiatusRAT tcp_forward function. This allows the hackers to forward their “beaconing” of a second infection through the compromised device before encountering an upstream Command & Control (C2) node. This also allows them to forward a command to a web shell of the upstream infrastructure via the affected router in the country where it is located. After that, a more passive agent helps to better disguise the original origin and thus bypass geo-fencing security measures.
Small number of affected routers
Currently, about 100 DrayTek routers have been compromised, Lumen indicated. This is between 1 and 2 percent of all DrayTek 2960 and 3900 routers currently connected to the Internet. According to security specialists, the cybercriminals are deliberately limiting their footprint to avoid detection. Regions affected by the attack include North and South America and Europe.
Also read: More than 11,000 WordPress websites compromised by malicious script
