Google Cloud is acutely aware that increasing cloud adoption simultaneously increases cloud threats. Cybercrime chases the trends found in enterprise IT environments, requiring new security measures to fight them off. That’s why the Chronicle cloud service is expanding, resulting in end-to-end coverage for threats.
Google Cloud makes a strong case for taking work away from independent IT teams. Instead of demanding resourcefulness from individual customers, it seeks to provide as many “packaged outcomes” as possible regarding cloud security. This should combine all SecOps workflows, from data analysis to detection & response.
This refers explicitly to TDIR: Threat Detection & Incident Response. In other words, detecting and adequately responding to cyber-attacks in one turnkey package. Since the Chronicle tool operates within Google’s own cloud, everything is integrated with its associated products: Security Command Center (SCC) Premium and Google Cloud telemetry can plug in directly with the new capabilities.
The update
Specifically, the Chronicle update offers many exciting additions. For example, there are now ready-made detection rules developed by Google’s internal threat research teams. Needless to say, they keep a close eye on potential Google Cloud vulnerabilities. The rules are context-sensitive, so they fit any specific organization.
The importance of context only becomes more apparent when we talk about “threat storylines”. It connects different things that may be relevant in a cyber threat, such as the accounts in question and compromised credentials.
With pre-built playbooks and best practices matching Google Cloud, users can respond “quickly and precisely.” This is assisted by Chronicle SOAR (Security Orchestration Automation and Response) which combines alerts from multiple sources.
In addition, Chronicle now normalizes telemetry from various cloud services, such as Cloud Asset Inventory, Google Kubernetes Engine, Google Compute Engine and more.
Zoom in
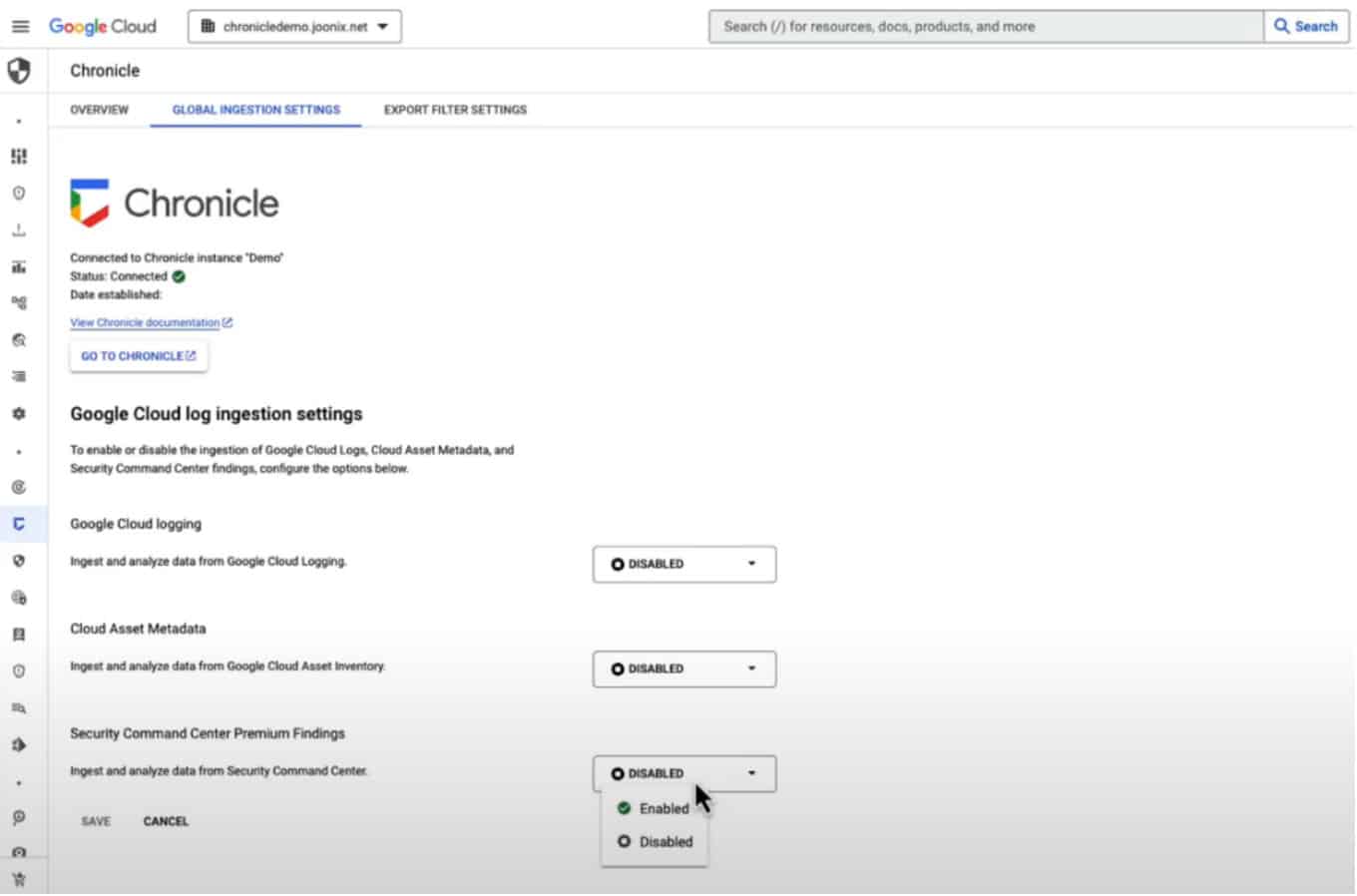
Google Cloud zooms in with a case study to demonstrate all this in practice. “Findings” can be enabled within the Security Command Centre, allowing access to the new capabilities.
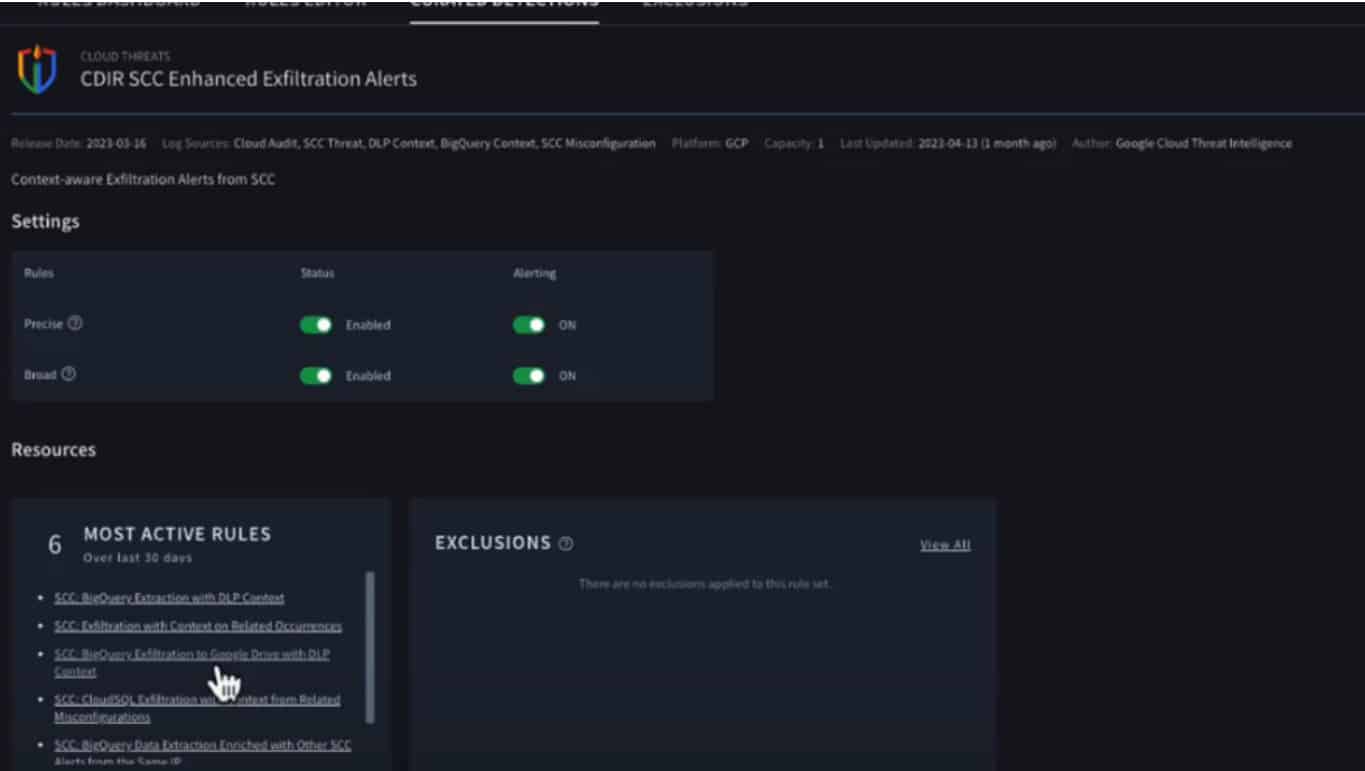
The following image then shows how one can see detection rules. What stands out is that we can include the most actively used rules in the lower left corner at a glance. Since so much of this operates automatically, it provides valuable insight into what is being executed.
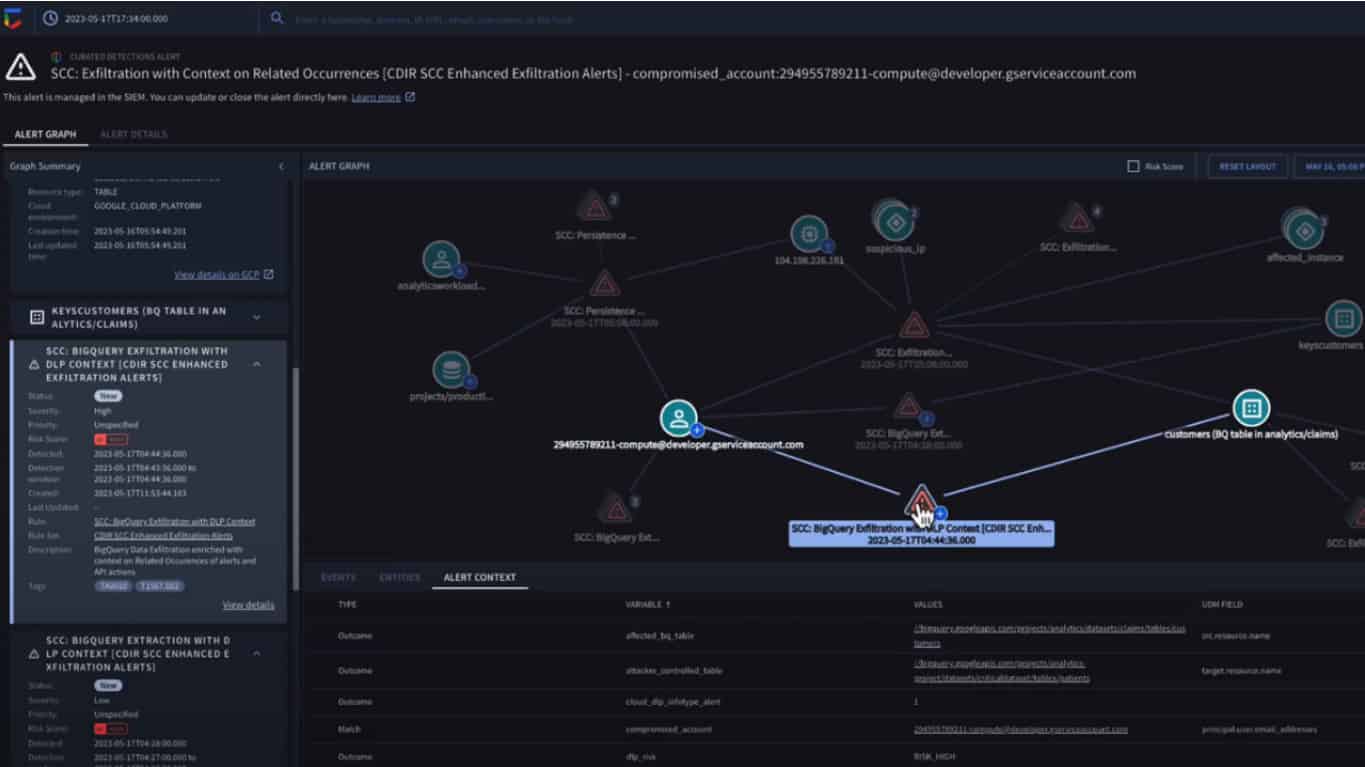
We then get to see the Chronicle Alert Graph, which visually represents the context surrounding an alert. Google Cloud has realized that we have little use for a stand-alone alert that does not provide any guidance. The example involves an exfiltration attempt from BigQuery. Chronicle has automatically seen that it involves cloud credentials in the form of encryption keys and e-mail addresses. This makes the severity of the cyber threat a lot more apparent.
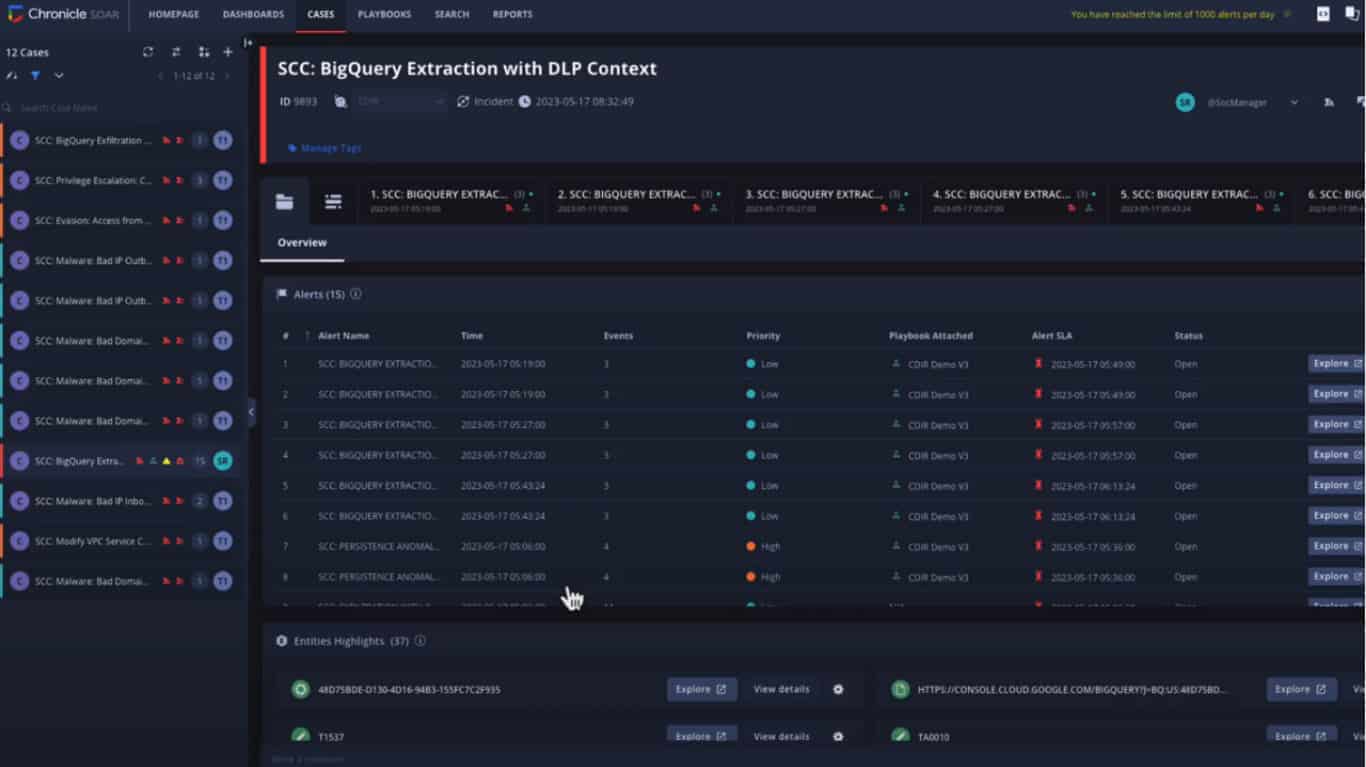
The last image shows a Chronicle Playbook. This automates response processes, collecting data and initiating remediation actions. This should keep the damage contained.
More can be learned about the new capabilities at Google’s own Security Summit session.
Also read: Cisco moves to better secure hybrid cloud environments and apps