The recent ‘PyLoose’ malware is the first Python-based fileless attack to target cloud-based workloads. This was discovered by security researchers at Wiz.
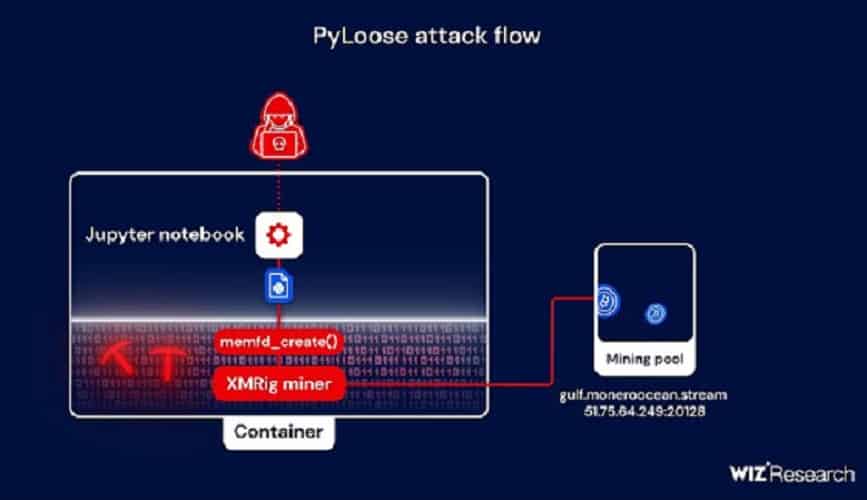
According to Wiz researchers, PyLoose is a Python-based fileless attack that targets cloud-based workloads everywhere. It was discovered on June 22. In a fileless attack, hackers do not rely on executable files to carry out the attack, but rather exploit the tools and features of software used by victims. This makes it easier for them to bypass any countermeasures and detection systems.
Directly in memory
PyLoose uses a Linux-based fileless technique, memfd, to load a so-called XMRig Miner directly into memory. This eliminates the need to write malicious payloads to a victim’s disk first. The technique exploits OS system features.
Infection with PyLoose begins via a public Jupyter Notebook service. The hackers then downloaded a fileless payload from a Pastebin-like website and downloaded it into Python’s runtime memory. This eliminates the need for disk storage and allows the attack process to be optimized by simplifying the command structure.
Who is behind the attack is not known. The complexity of the attack suggests that it involves highly trained and knowledgeable attacker(s).
Possible solutions
Wiz indicates that the attack can also be countered. They recommend not using public services such as Jupyter Notebook, as they may result in (remote) code execution. In addition, robust authentication, such as using MFA and a centrally managed identity platform, offer further protection.
Tip: Microsoft won’t let hackers mess with detection tool Sysmon any longer