The TP-Link Tapo L530E smart lamp not only provides light, but also allows hackers to steal WiFi passwords via the accompanying Tapo mobile app. This was discovered by Italian and British researchers.
The researchers from the Universita di Catania and University of London discovered four key vulnerabilities in the TP-Link Tapo L530 smart lamp and the mobile app that controls it.
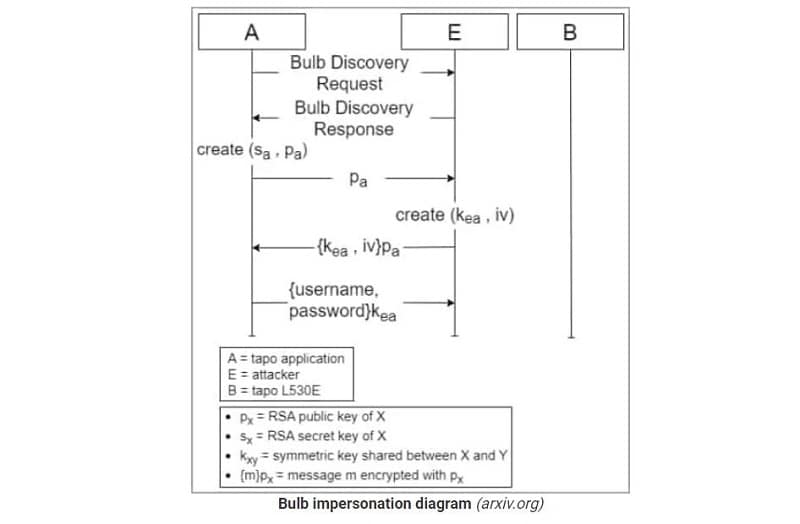
The first of these involves a faulty authentication of the lamp that lets hackers impersonate the lamp during a session key exchange. This allows them to retrieve Tapo user data and manipulate devices.
The second vulnerability involves a hard-coded short checksum secret. Hackers can obtain it through a brute-force attempt or by decompiling the Tapo app. The third problem deals with the lack of randomness during symmetric encryption. This makes the encryption scheme predictable and thus crackable.
The fourth and final vulnerability concerns the lack of checking the freshness ban received messages, keeping session keys valid for 24 hours and allowing hackers to replay messages during this period.
Attack scenarios
Attack scenarios are conceivable due to the vulnerabilities, according to the researchers. The most worrisome is that of impersonating the smart bulb and retrieving Tapo user data through the first and second vulnerabilities. When hackers gain access to the Tapo app, they can steal the victim’s WiFi SSD and password and thus gain access to all devices present on the network.
However, this does require the smart bulb to be in setup mode. Hackers can, however, de-authenticate the smart bulb, forcing users to reset the bulb, thus giving access to the necessary setup mode.
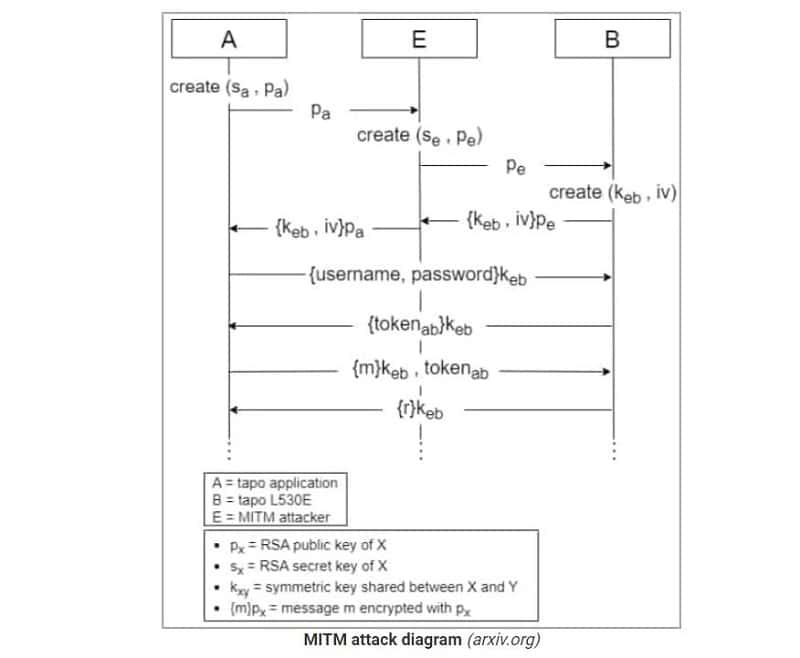
MITM attack
Another attack scenario is a Man-In-The-Middle (MITM) attack. This is executable with the first vulnerability found and vulnerability number 4, among others, indicate the researchers from both universities.
TP-Link has been notified by the researchers of the vulnerabilities for its Tapo L530 lamp and the associated mobile management app. Whether fixes for these have already been implemented is unknown.
Also read: Microsoft Defender for IoT soon to scan Linux devices