Nozomi Networks discovered vulnerable third-party libraries in hundreds of IoT devices from well-known manufacturers. The vulnerability allows cybercriminals to assign fraudulent IP addresses.
According to the security specialists, hundreds of IoT devices suffer from a vulnerability that allows hackers to connect IP addresses to malicious servers that appear to be legitimate. Attackers that have access to the connection between devices and the Internet can spoof DNS requests and take over.
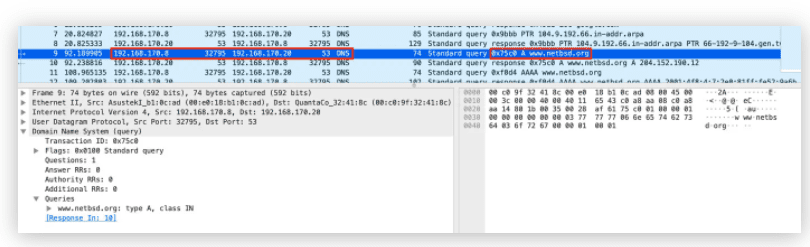
uClibc and uClibc-ng libraries
The vulnerability lies within two uClibc libraries. These libraries serve as an alternative to the standard C library for embedded Linux code. Nozomi Networks notes that the vulnerability is related to the predictability of ports and transaction numbers assigned to lookups.
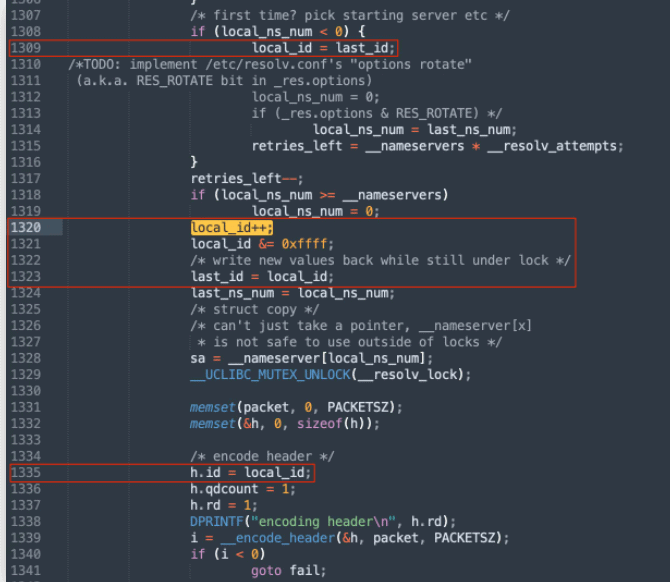
Various manufacturers affected
Various vendors use the affected libraries. Linksys with its WRT54G router, NETGEAR with the WG602 wireless router, almost all Axis network cameras and the Tuxscreen Linux Phone. Netgear issued a security alert.
A number of software apps and modules were affected as well, including embedded Gentoo, Buildroot and LEAF Bering-uClibc. The latter is a successor to the Linux Router Project, which supports Linux on gateways, routers and firewalls. This means that the scope of the vulnerability may be larger than presently known.
Tip: Critical vulnerabilities in large number of Aruba and Avaya switches
