Linux devices connected to the Internet of Things (IoT) are vulnerable to NoaBot. This botnet is linked to crypto-mining activities and is another form of the previously known botnet Mirai. What sets NoaBot apart is its ability to duplicate itself, and that is also where its greatest danger lies.
A new version of the Mirai botnet surfaced last year. It is a modified version called NoaBot. This botnet targets Linux devices ranging from servers to cameras. Researchers from Akamai set up an investigation into NoaBot and saw the first activities of the botnet in January 2023. The researchers know of more than 800 infected IP addresses with infections in all places of the world.
Misused for crypto-mining
The hackers behind Mirai were interested in creating a large net of devices to carry out DDoS attacks to take down websites and online services. The organization behind NoaBot is trying to collect devices to carry out crypto-mining activities. For the victim, this initially means an increase in the use of electricity and data.
The malware is said to be a variant of XMRig, which is available through open source. Furthermore, there are also known cases of NoaBot transmitting the worm P2Pinfect. P2Pinfect is a malware that targets Redis. Redis is an open-source software deployed as a caching technique to make Web sites load faster. However, the biggest goal the hackers behind P2Pinfect seemed to want to achieve in August 2023 was the same and focused on creating a botnet.
Duplicates itself
NoaBot does find its beginnings in the existence of Mirai. This is because the hackers behind Mirai released the underlying source code, allowing hackers to freely design variants of the botnet.NoaBot was created that way.
This variant was designed so that it could abuse Linux devices to infect other vulnerable devices. Actually, the same feature is found with Mirai, but NoaBot does not perform the duplication by breaking into devices protected by default passwords. Instead, it guesses passwords that secure SSH connections.
Check your devices
Researchers at Akamai made available with the report a tool that holders of Linux IoT devices can use to check that their devices are not part of the botnet.
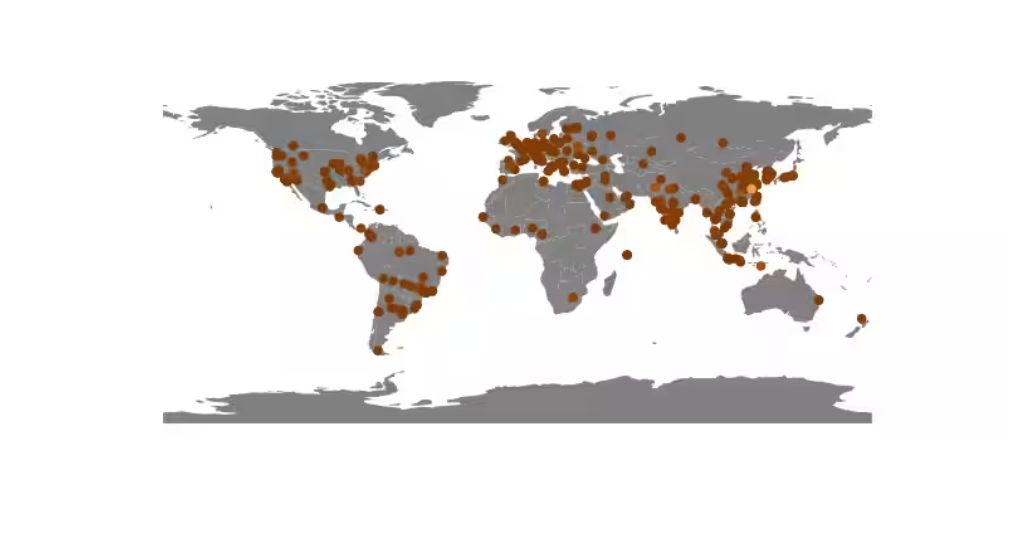
The directory indicates where the infected devices are located. Source: Akamai
Also read: Hackers can expand Mirai botnet by at least 7,000 devices
