The open-source object storage solution MinIO has a number of vulnerabilities that hackers are now actively exploiting. This was discovered by researchers from Israel-based Security Joe’s.
According to Security Joe’s, two critical vulnerabilities have been found in the open-source object storage service. Among other things, MinIO offers compatibility with Amazon S3 and functionality for storing up to 50 TB of unstructured data, logs, backups and container images.
The service is primarily a low-cost storage option for large AI/ML models and data lake applications, among others.
Two critical vulnerabilities
According to Security Joe’s, critical vulnerabilities CVE-2023-28432 and CVE-2023-28434 allow hackers to view sensitive information, run arbitrary code and possibly take over servers.
Also read: Chrome extensions steal passwords in plain text
The researchers came across the vulnerabilities during a security incident response. The hackers attempted to install a modified version of a MinIO application known as Evil MinIO. This malicious variant is available on GitHub.
As part of the attack, the malicious application chains together the CVE-2023-28432 information disclosure vulnerability and the CVE-2023-28434 vulnerability. This replaces the MinIO software with custom code that adds a remotely accessible backdoor to the affected system.
The vulnerabilities have been known for several months. MinIO released patches for them in March this year.
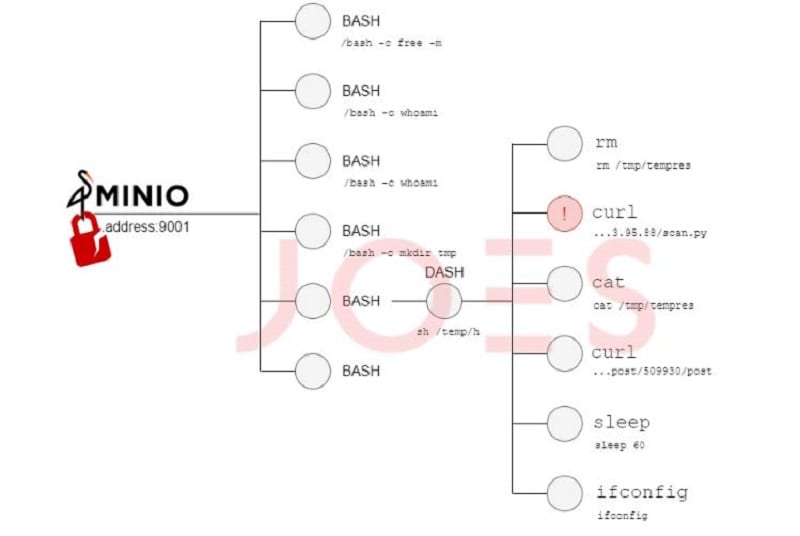
Attack path
The current attack starts via a social engineering campaign for DevOps engineers. These must be convinced to downgrade to an earlier version of MinIO affected by the two vulnerabilities.
The hackers then gain access to administrative privileges that allow them to access the MinIO console via the MinIO client. Subsequently, they modify the software update URL to an environment controlled by them, allowing them to push the malicious version. At the same time, the legitimate .go source code file is also replaced with the modified code.
After breaching the affected object storage system, the software acts as a backdoor to a C&C server that allows hackers to install other malicious software and code.
Large attack surface
The vulnerability affects all MinIO systems up to version RELEASE.2023-03-20T20-16-18Z. Security Joe’s warns that there is a large attack surface. Meanwhile, 52,125 MinIO instances are accessible via the public Internet.
About 38 percent of these instances are running a nonvulnerable version of the open-source object storage environment. This means that 62 percent are vulnerable, though.