The hotel industry has been facing a major global advanced phishing attack since June. This is a two-step attack that uses vulnerabilities in DNS protocols.
According to researchers at Akamai, a large advanced phishing attack has been underway since June that specifically targets the hotel industry. Based on cases from Switzerland, Italy, Canada, Argentina, Hong Kong and Singapore, among others, the attack is taking place worldwide.
The attack mainly uses vulnerabilities in DNS protocols that the hackers want to use to disguise their original location. They also want to add more complexity to hinder fighting the hacking attack as much as possible.
Within this framework, several techniques are used by the attackers, including typosquatting, combosquatting and levelsquatting.
Attack pattern
The discovered phishing attack is twofold in design, Akamai experts further discovered. Initially, the hackers try to entice hotel staff. They do this, for example, by making fake online bookings for hotel rooms.
After these bookings, the hackers send hotel staff follow-up emails that contain malware, including through links or included photos. Malware thereby focuses on stealing the data from the attacked hotels.
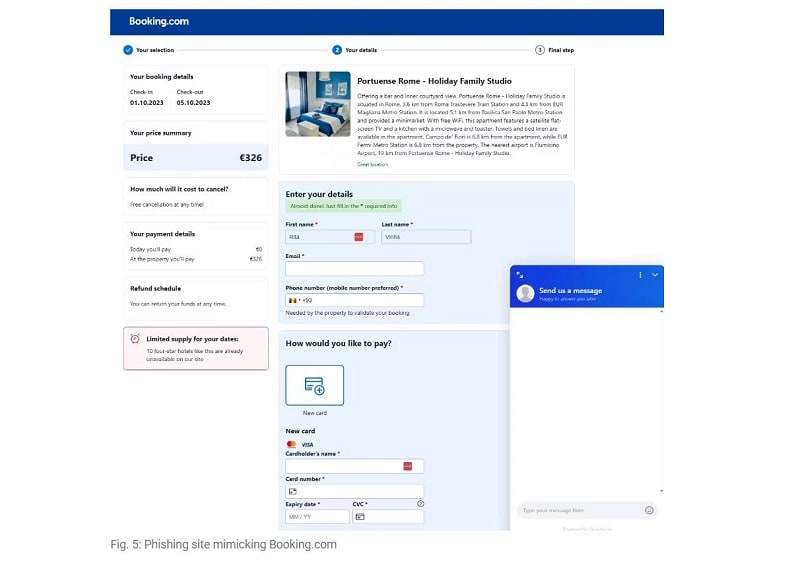
The second phase of this attack targets the guests of these hotels. Especially individual customers who use the hotels’ online services. For this purpose, the hackers set up fake pages of the previously affected hotels that appear lifelike.
The customers who land on these pages and use the online (booking) services are also sent emails containing malware. In addition, the hackers even created an online chat window that makes the spoofed hotel pages appear lifelike. With all these features, the hackers behind the global campaign want to steal credit card data.
So for these attacks, the hackers use the aforementioned DNS vulnerabilities. For example, these should quickly generate domains that the hackers can briefly use to host their malicious pages and the malware applications located on them.
Hackers not tracked
Who is behind the attacks is unknown. DNS data and IP addresses seem to point to hackers from Russia, but this could also be a smokescreen, according to Akamai. Most of the malicious DNS traffic for this case originated from Switzerland, Hong Kong and Canada.
Also read: HR topics used the most as attack method in phishing attacks