A new phishing campaign that aims to install a rogue extension specifically targets administrators of WordPress websites, reports Wordfence. Hackers are allegedly posing as the “WordPress Security Team” in the process.
According to Wordfence, a phishing campaign is underway that targets administrators of WordPress sites. In their campaign, the hackers are trying to get administrators to install a malicious extension, which later functions as a backdoor.
Attack path
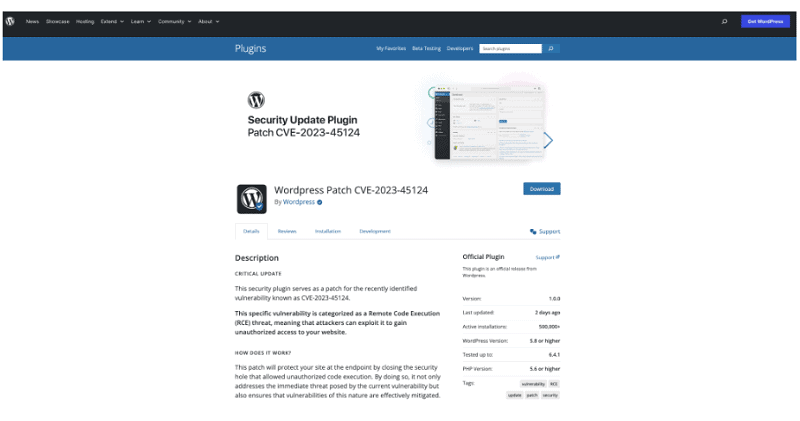
On behalf of the “WordPress Security Team,” the hackers send a phishing email to administrators warning them that their site has a particular vulnerability, including a made-up CVE number. They are advised to install a plugin linked in the email.
The link points to a .org site containing the WordPress name and shows an almost identical version of the official WordPress site.
However, the ”recommended ”Security Update Plugin” extension is a rogue extension, which adds a malicious ”wpsecuritypatch” manager to the affected WordPress site.
The extension includes functionality to hide itself and, in turn, installs a PHP backdoor with a hardcoded password. In this way, the hackers gain complete control over the affected website.
Alertness desired
Wordfence itself will soon come out with a deeper analysis of this phishing campaign. In any case, the security specialists warn WordPress administrators to pay close attention to this phishing email, do not click on links, including the Unsubscribe link, or install the extension.
Also read: Bug in WordPress plugin exposes 600,000 vulnerable websites