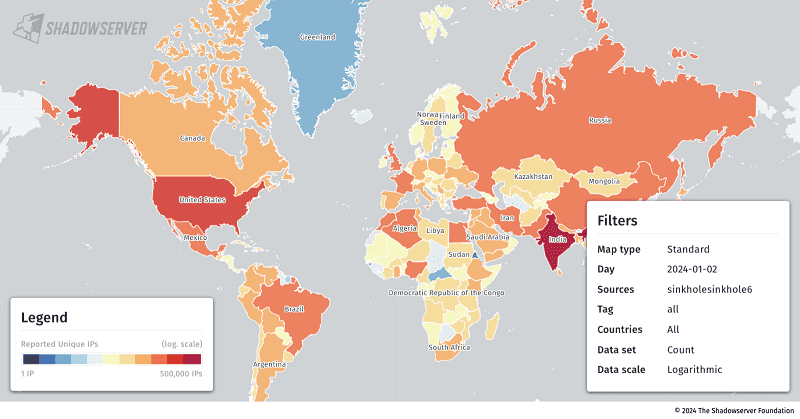
A global scan shows that about 11 million servers are still vulnerable to the recently discovered Terrapin SSH vulnerability. However, security experts estimate that its impact is not significant, despite the strong possibility that the vulnerability will remain present for several years.
The research was conducted by Shadowserver, writes Ars Technica. It shows that around 11 million online Secure Socket Shell (SSH) servers worldwide are still vulnerable to the recently discovered Adversary-in-the-Middle (AitM) attack vector Terrapin, also known as CVE-2023-48795.
This method of attack allows hackers to gain a foothold in attacked networks. From that position, a threat actor can compromise the integrity of SSH sessions. In this way, the hackers are able to secretly intercept communications between senders and receivers, alter its contents and pretend to be both sender and receiver.
Also read: Online data transfer not always secure with SSH protocol despite encryption
Vulnerable encryption methods
Specifically, the Terrapin vulnerability is capable of compromising or altering data during the “handshake”. That is the moment when sender and receiver establish a secure connection and exchange the necessary encryption parameters to do so. By changing sequence numbers, data can be accessed or stolen without senders and receivers noticing.
The attack technique is said to work better with certain encryption mechanisms than the others, however. Vulnerable are the encryption mechanisms ChaCha20-Poly1305 or CBC with Encrypt-then-MAC. About 77 percent of all SSH servers are equipped with exactly these encryption methods.
11 million servers and more than 50 applications
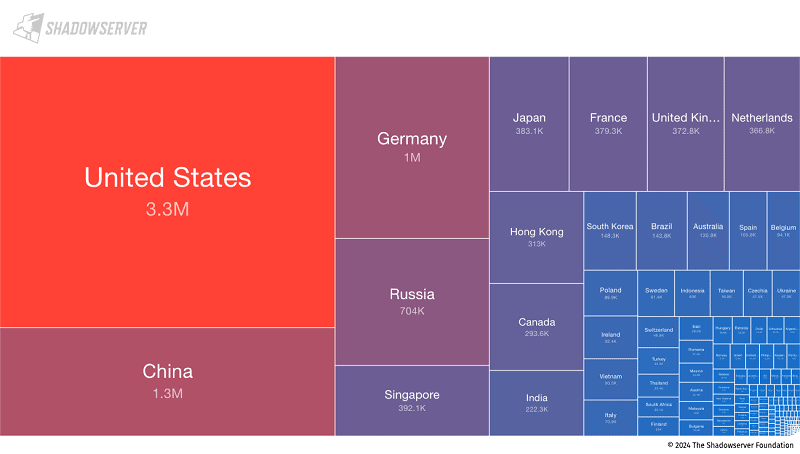
The ShadowServer researchers found that all of the discovered vulnerable SSH servers use the above encryption methods. A third of the server addresses found, 3.3 million in total, were found in the U.S., followed by China, Russia, Germany, and Singapore.
The researchers also found that several applications using the SSH protocol were vulnerable in some way. The most vulnerable application, AsyncSSH, was found on 53 SSH servers.
AsyncSSH has since been patched and others of the Top 50 vulnerable applications also have patches against Terrapin available, but not all of them yet.
No major impact expected
As for the likelihood of Terrapin having as big an impact as Citrix Bleed did last year, ShadowServer specialists are thankfully a lot more positive. Executing a Terrapin attack is a lot more complicated and ensures that the impact will ultimately be a lot less.
However, they do indicate that because of the large number of potentially vulnerable servers, 11 million, the method of attack will remain present for several years. Nevertheless, administrators are urged to patch as soon as possible, though.