5,379 GitLab instances are still at risk. These instances may be affected by the recently discovered GitLab account vulnerability. ShadowServer research shows that accounts can still be taken over.
Recently, GitLab was affected by the critical vulnerability CVE-2023-7028. GitLab has since fixed this with a patch. However, ShadowServer research shows that many users have yet to install this patch. Potential risks include supply chain attacks, disclosure of proprietary code, API key leaks and other malicious activities.
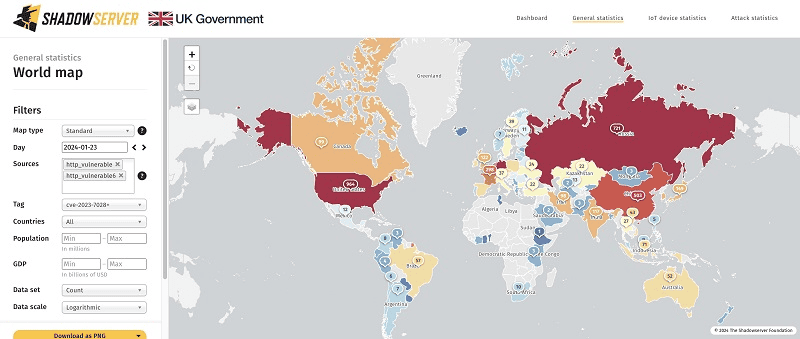
Most vulnerable instances are in the U.S., totaling 964, followed by Germany (730), Russia (721), China (503), France (298), the UK (122), India (117) and Canada (99). However, no specific breaches have been reported at the time of writing.
Features CVE-2023-7028
This vulnerability for GitLab instances allows attackers to perform a so-called zero-click attack to take control of instances.
This vulnerability allows hackers to send password reset emails for an attacked GitLab account to an email address they control. This way, they can then change the password and take over the account. However, when 2FA is enabled, this is blocked.
Fixes already released for some time
The problem occurs in GitLab Community and Enterprise Edition version 16.1 for 16.1.5, version 16.2 for 16.2.8, version 16.3 for 16.3.6, version 16.4 for 16.4.4, version 16.5 for 16.5.6, version 16.6 for 16.6.4 and version 16.7 for 16.7.2.
Two weeks ago, patches were released for versions 16.7.2, 16.5.6 and 16.6.4, as well as backporting patches for versions16.1.6, 16.2.9 and 16.3.7.
GitLab urges companies to still check their systems after implementing the updates for possible changes to their development environment, including source code and potentially modified files.
Also read: GitLab accounts vulnerable to takeover, patch available