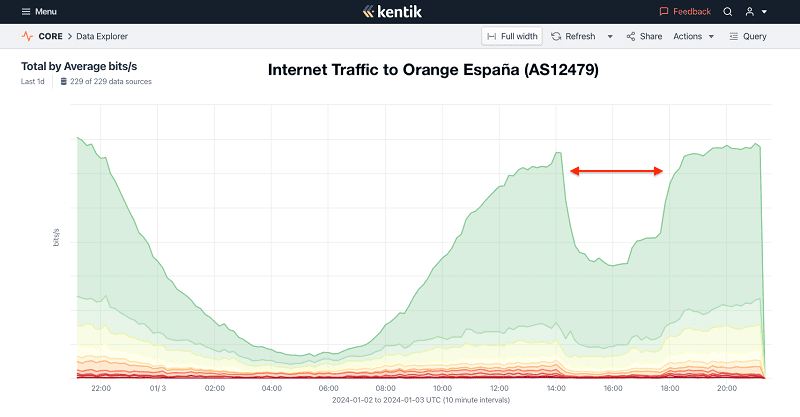
A hacker last week managed to take down the network of Orange España, the country’s second-largest mobile operator. He hacked the system using a very weak password that gave access to the global routing table that controls the network for delivering the mobile operator’s internet traffic.
The hacker Snow managed to access the so-called RIPE Network Coordination Center (RIPE NCC) account of the Spanish branch of Orange using the weak password “ripeadmin”. This is what the hacker himself claims in a post on X. The RIPE NCC is a regional internet registry that manages IP addresses and assigns them to ISPs, telecom operators and companies that have their own network infrastructure.
According to security researchers, Snow had purchased the password on the internet after it was stolen from an Orange computer earlier last year. On the dark web, thousands of RIPE login credentials were allegedly offered. So, not only was the password simple because of the reference to the network being logged into. Also, Orange had been using the same password for an extended period of time.
Hacker fabricated fake applications
After Snow gained access, he tried to outage the network. This was done by making changes to the global routing table with which Orange determines which backbone provider takes its internet traffic to another continent. This happens with the so-called BGP protocol.
Snow’s attack added some new Route Origin Authorizations (ROAs) that connect one regional network to the rest of the internet. This allows “autonomous systems” to designate other autonomous systems or large chunks of IP addresses to deliver internet traffic to other parts of the world.
Previous attempts made by the hacker had no effect; these were mitigated. So Snow, in the end, decided to add about five ROAs with a false origin. In this case, an origin that had nothing to do with Orange España.
This triggered a new protection feature in the BGP protocol, Resource Public Key Infrastructure (RPKI), which caused the various backbone providers to deny requests from Orange España. As a result, a major outage occurred on Orange España’s internet traffic.
Network routing settings restored
Eventually, Orange España managed to regain control of the compromised RIPE NCC account. The mobile operator was then able to restore service by publishing the correct ROAs.
Some rogue ROAs are still present in the network. This is not a problem, they are harmless because legitimate ROAs have been published with the correct origin.
Also read: 123456 most common password of 2023