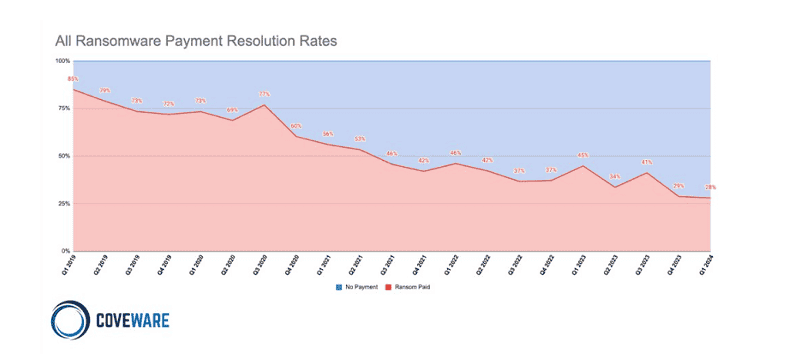
Victims of ransomware attacks are less likely to pay cybercriminals to release the encrypted or stolen data. This is according to Coveware research in a quarterly report.
The researchers state that in the first quarter of 2024, 28 percent of companies affected by ransomware paid the requested ransom, compared to 29 percent in the last quarter of 2023.
Companies are paying less because they protect themselves more against these attacks. They are also increasingly able to perform recovery operations themselves and, consequently, are less dependent on a decryption key.
In addition, companies are increasingly being legally forced not to give in to ransomware criminals. For example, the state of Florida in the U.S. prohibits responding to ransomware attacks, as does Australia.
Furthermore, companies often do not pay because cybercriminals don’t keep their end of the agreement anyway. For example, they publish or otherwise trade the stolen data after payment despite promising not to do so.
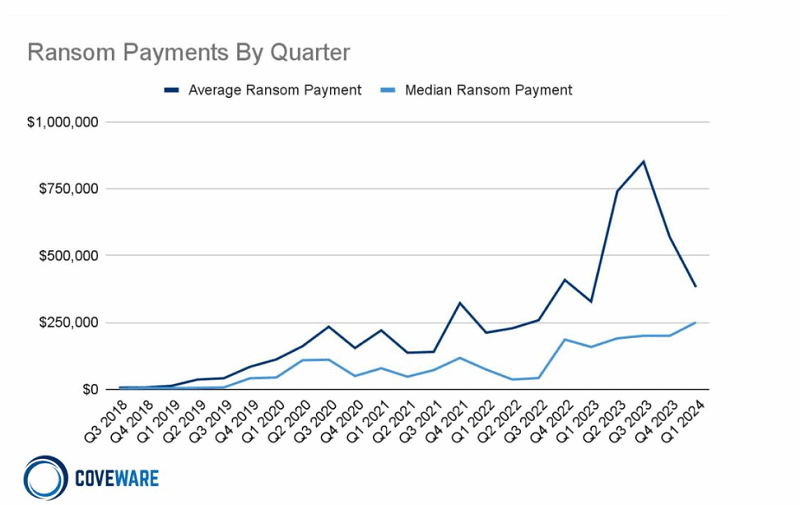
The average amount of demanded ransom drops
The average ransom price in the past first quarter was $382,000 (358,000 euros), down 32 percent from the previous quarter. However, the median was 25 percent higher at $250,000.
According to the Coveware research, part of the reason the average ransomware ransom price is falling is because criminals recognise they no longer can charge astronomical sums that companies cannot cough up anyway. As a result, criminals are now switching more frequently to asking for more reasonable ransom amounts.
The study states that the drop in ransom prices could be due to fewer ‘high-value’ targets willing to be extorted and, therefore, pay ransoms.
The researchers state that ransomware is still a significant threat and that more than $1.1 billion in ransoms was still paid last year.
Read more: Ransomware payments reach record high: more than 1 billion euros
Ransomware groups and attack vectors
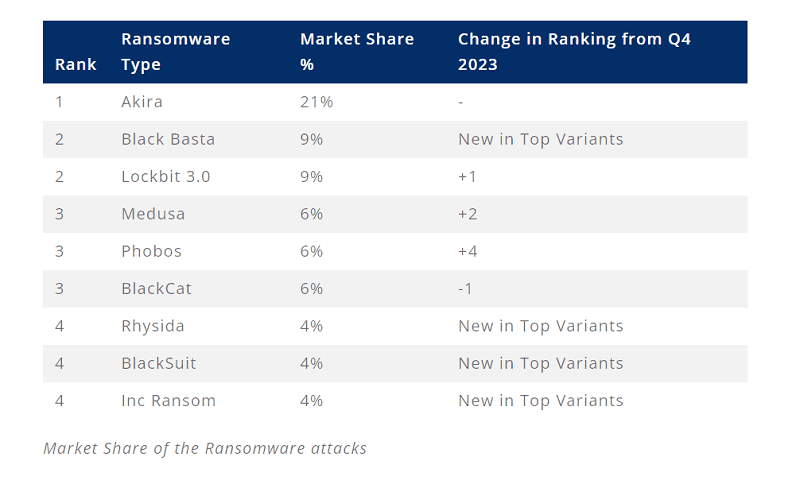
Coveware also examined the most popular perpetrators of ransomware attacks in the first quarter of this year. The Akira group was the top perpetrator, followed by Black Basta and LockBit 3.0 in joint second place. LockBit 3.0 took a big hit due to actions by the FBI and other security authorities.
The Medusa, Phobos and AHV/BlackCat ransomware gangs share third place. The latter gang, in particular, lost a lot of ground, partly due to payment disputes with affiliates and an exit strategy.
Last, the researchers looked at the most common attack vectors. Remote access vulnerabilities, such as CVE-2023-20269, CVE-2023-4966, and CVE-2024-1708-9 were the biggest cause. New attack vectors are also slightly on the rise. Ransomware attacks via phishing and software vulnerabilities decreased over the past quarter.
Also read: LockBit falters under pressure from competitors and copycats