At least 165 organizations have been affected by a recent series of hacking attacks against customers of cloud company Snowflake. So says security firm Mandiant. The company is working with Snowflake to investigate the attacks. There is no evidence hackers compromised Snowflake’s systems, the attackers allegedly gained access through captured login information that, in some cases, is years old.
Companies affected by the attacks include Ticketmaster and Advance Auto Parts. At Ticketmaster, criminals captured the data of 560 million users and at Advance Auto Parts, they pilfered 3 TB of customer, inventory, and sales data, among other things. The bank Santander also reported a leak. However, Mandiant did not disclose whether this was part of the same series of attacks.
Mandiant has identified the hacker group responsible as UNC5537. The Google-owned company has been working on the case since April. The cybersecurity company discovered stolen data from a Snowflake environment belonging to an unnamed organization, the company reported in a blog post. More Snowflake customers appeared to be affected in May. Mandiant then notified Snowflake, and the companies began an investigation together. On May 30, they made their preliminary conclusions public.
No vulnerability at Snowflake’s end
So far, there seems to be no leak on Snowflake’s side, which the company has already clarified in its communications. The stolen credentials probably originate from info stealer campaigns from sometime years ago, in which criminals used malware to steal data such as login credentials, personal identification information and other confidential information.
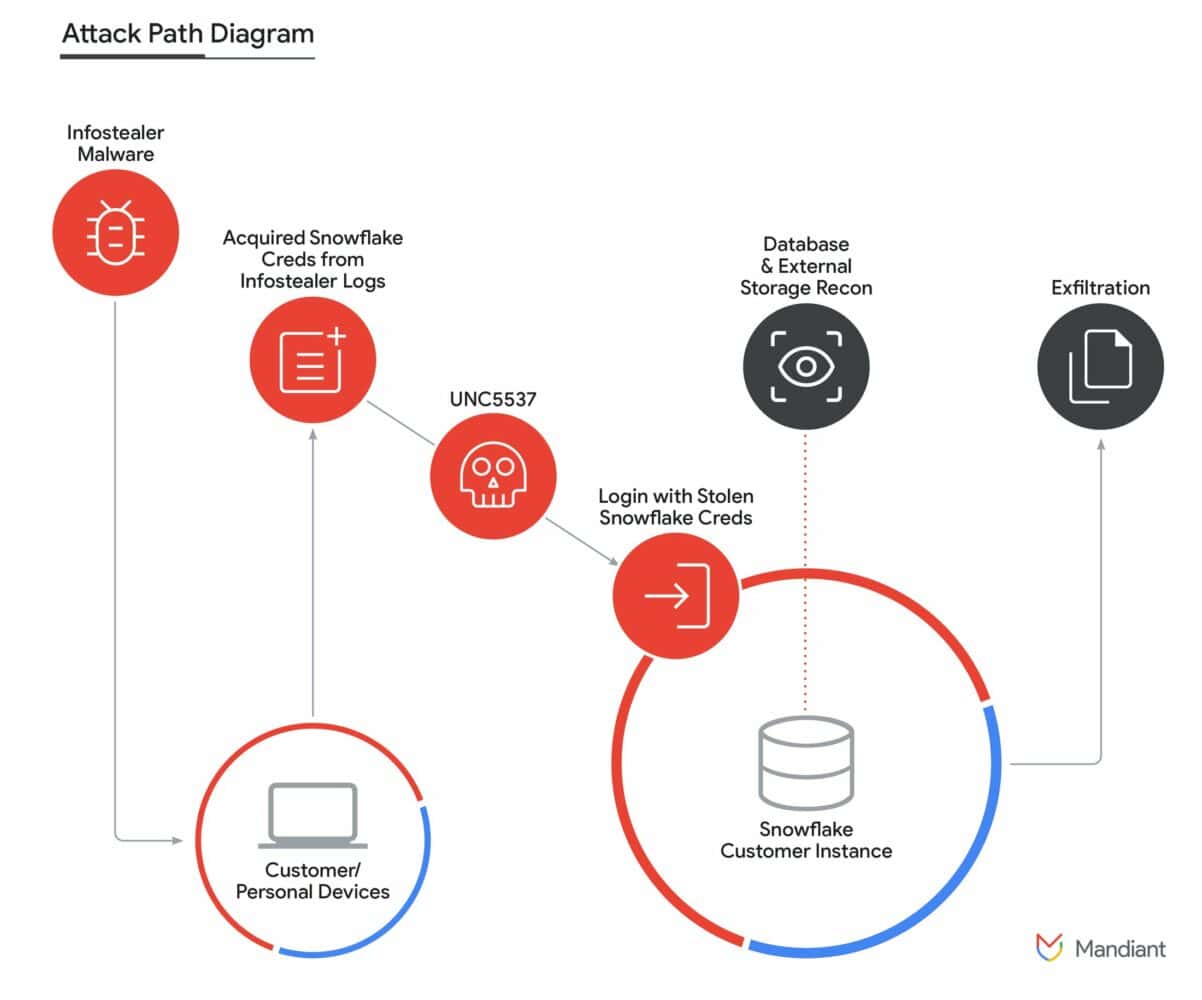
This data is quite old in some cases, with the stolen data going back to at least 2020. The data is still usable because its owners didn’t bother to renew or rotate the credentials in the interim. Also of note is that the affected users failed to use multifactor authentication and were not using network allow lists, where users can normally log in only from a trusted location.
At least 79.7 percent of the account credentials have previously surfaced in lists of captured data. On Friday, Snowflake reported that it is developing a plan to require customers to use advanced security controls like multifactor authentication. The company is also offering additional guidance on protecting against hacking attempts. In addition, it is insisting on a system of ‘least privilege’, in which organizations take a stricter look at who should have access to sensitive data in the first place.
Also read: Ticketmaster incident shows: attackers no longer break in, but log in
