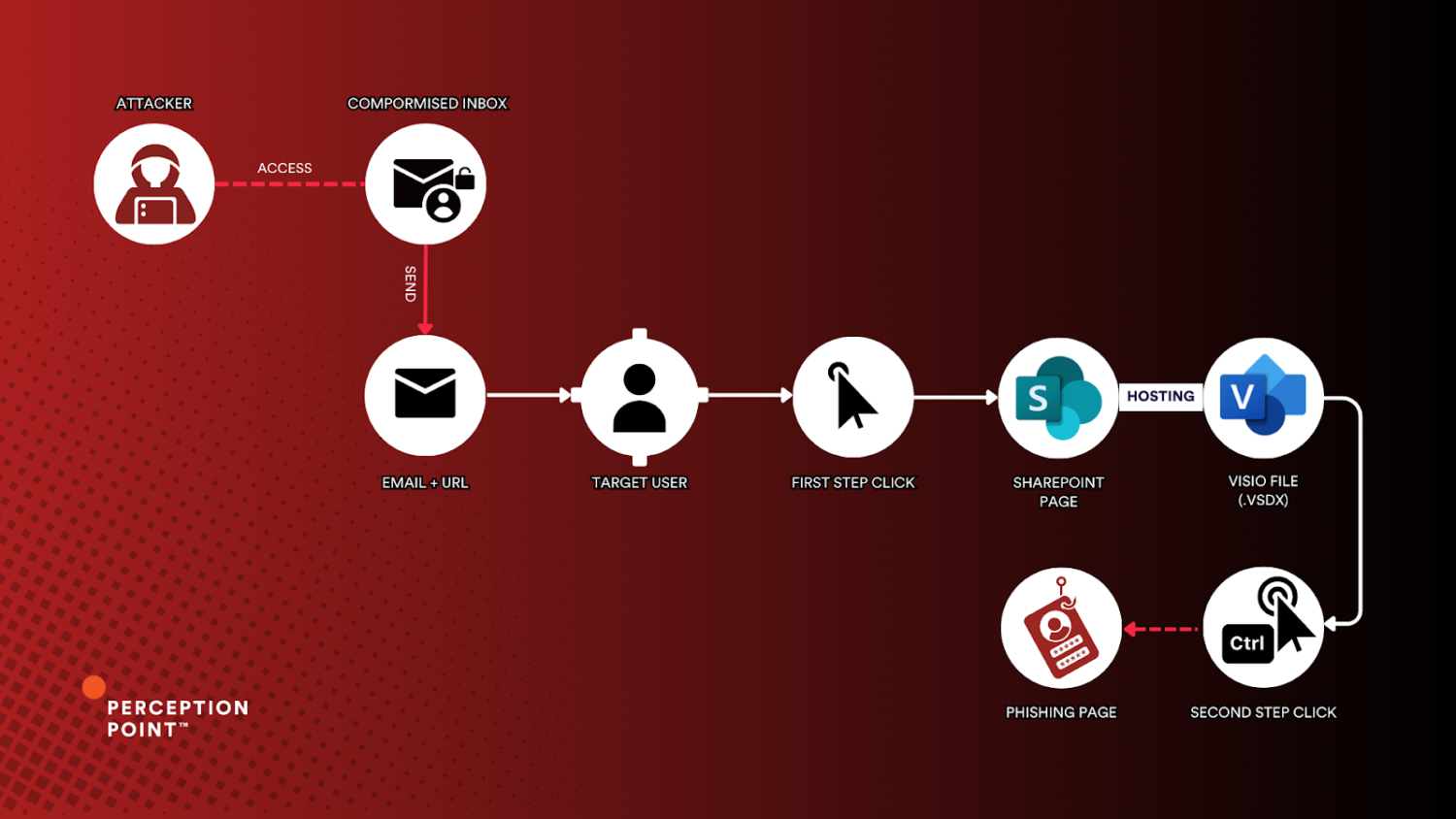
Hackers are increasingly using files for Microsoft Visio to lure unsuspecting computer users to phishing sites. These utilise fake documents in compromised Sharepoint environments. Eventually, victims get redirected to a fake login page for Microsoft 365.
According to cybersecurity specialist Perception Point, the campaign concerns a so-called two-step attack pattern. Hackers first send emails through compromised accounts, which include a link to a Visio file in an (also hacked) Sharepoint environment. The malicious parties use links in those files to lure unsuspecting recipients to the actual phishing site.
The whole purpose of this multi-layered approach is to appear as trustworthy as possible. First, the initial email arrives via a ‘real’ email address. It’s a compromised address, but the recipient doesn’t know that. The malicious party also bypasses standard security checks this way. The messages are typically about purchase orders or business proposals, so this part of the operation uses well-known social engineering tactics.
Compromised Sharepoint environment
The emails often contain an .eml file or Outlook email message. Basically, they’re emails with a saved email message attached to them. This attachment contains a link to a file in a Sharepoint environment, which is, in many cases, also compromised.
The document in the Sharepoint environment is a .vsdx file, a document type for Microsoft Visio. Visio is a programme for quickly creating flowcharts, diagrams, tables, organization charts, and other visual aids for business purposes. These documents are interactive and may include buttons that link to another document or website. The hackers hide their phishing links in exactly these buttons.
Creating trust
By using .vsdx files, the hackers try to inspire trust. For example, these can be styled with the corporate identity of the company whose systems have been hacked. Such documents also include instructions to hold down the ‘control’ button when clicking the link. The reason for this is simple: that way hackers make sure it is a human opening the link and not a bot or other automated process.
The final step is the fake Microsoft 365 environment that opens, where the victim supposedly has to log in. If they do, the login credentials are captured. To stay ahead of such phishing attempts, Perception Point recommends measures such as Dynamic URL Analysis and AI security tools that specialize in malicious object detection.
