A new phishing method aims to sidestep the two-step verification of Instagram accounts. A misleading email message and login page lets users unintentionally reveal their credentials and a temporary six-digit backup code.
The findings come from Trustwave, which previously described another method to take over Instagram accounts. With “Insta-Phish-A-Gram,” scammers obtained their victims’ phone numbers in 2022, but now backup codes are not safe either.
Old tactics, no less dangerous
The setup of the phishing method is relatively simple. First, the attackers send an email purporting to be from Instagram parent company Meta. In it, users are told that their account may have violated copyrights. The user is prompted to log in within 12 hours using a specific link to stop their account from being lost. That sends unsuspecting victims to a realistic-looking scam version of a Meta website.
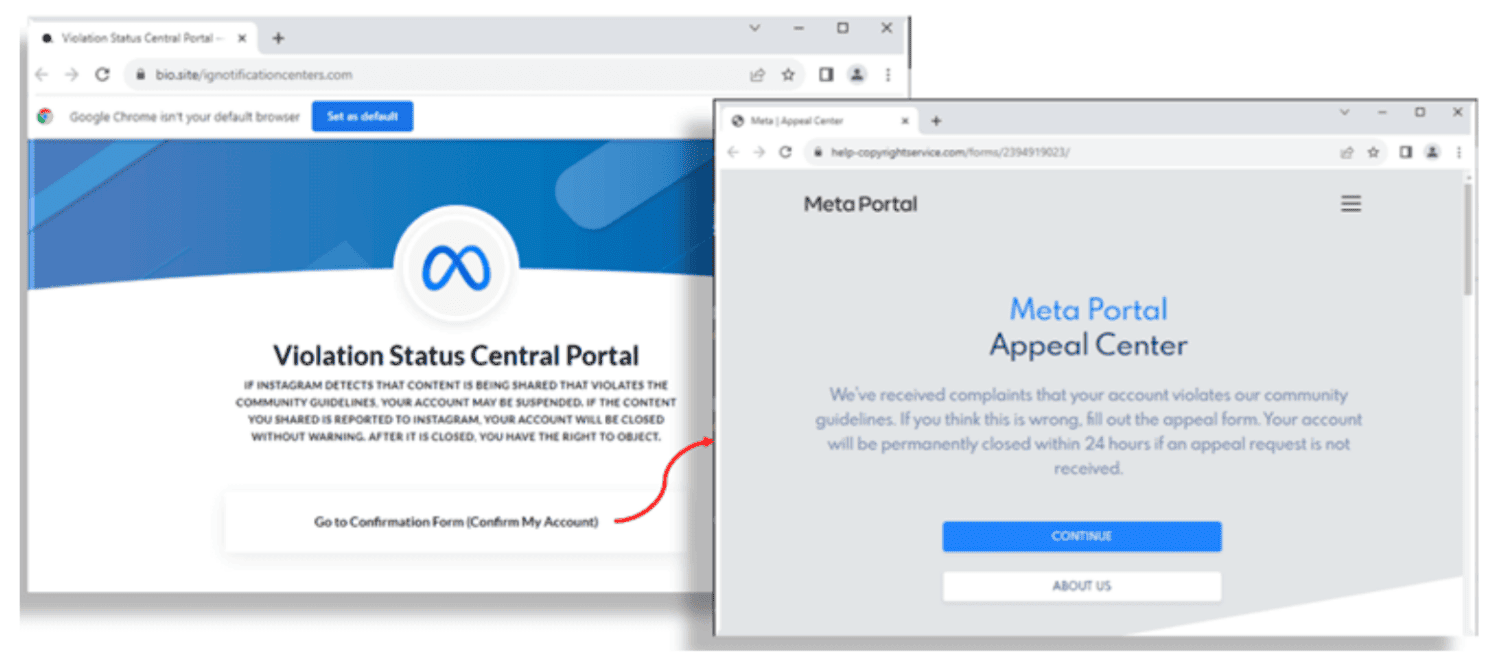
After a redirect, the user lands on the actual phishing page. Here, the website asks for their username and password (twice). They are also asked to indicate whether two-step verification is turned on. Then, a backup code can be requested, which is needed to log in from an unknown device. The end result is that the scammers can obtain all the information to log into the victim’s account.
No advanced techniques
It’s not the most sophisticated technique for scammers to use. Still, even with a small success rate, there is the potential to hijack countless accounts. After all, Instagram is said to have a user base of 2.4 billion, so there will always be someone who falls for the deception.
We recently saw more advanced techniques utilizing so-called “SMTP smuggling”, although it was thankfully deployed by researchers rather than criminals. This allows attackers to make it appear that their phishing emails come from legitimate addresses.
Also read: Decades after its debut, SMTP still enables new phishing techniques
