A new form of e-mail spoofing was revealed this week: “SMTP Smuggling.” The vulnerability allows threat actors to produce highly believable phishing emails. Although it seems decades past the time to move away from the ancient protocol, SMTP is here to stay.
The new method bypasses email protection tools such as DMARC and SPF. Messaging services from the likes of Microsoft, GMX and Cisco were found to be susceptible to zero-days that allow someone to send emails with a fake address appearing to the recipient. Researcher at SEC Consult Timo Longin explains that all kinds of addresses are possible to fake, citing ceo@microsoft.com as an example. Numerous domains such as amazon.com, irs.gov and cisco.com were found to allow for spoofed senders to be used with the exploit. Along with some HTML code, the technique allows for some very convincing phishing emails, the research results show.
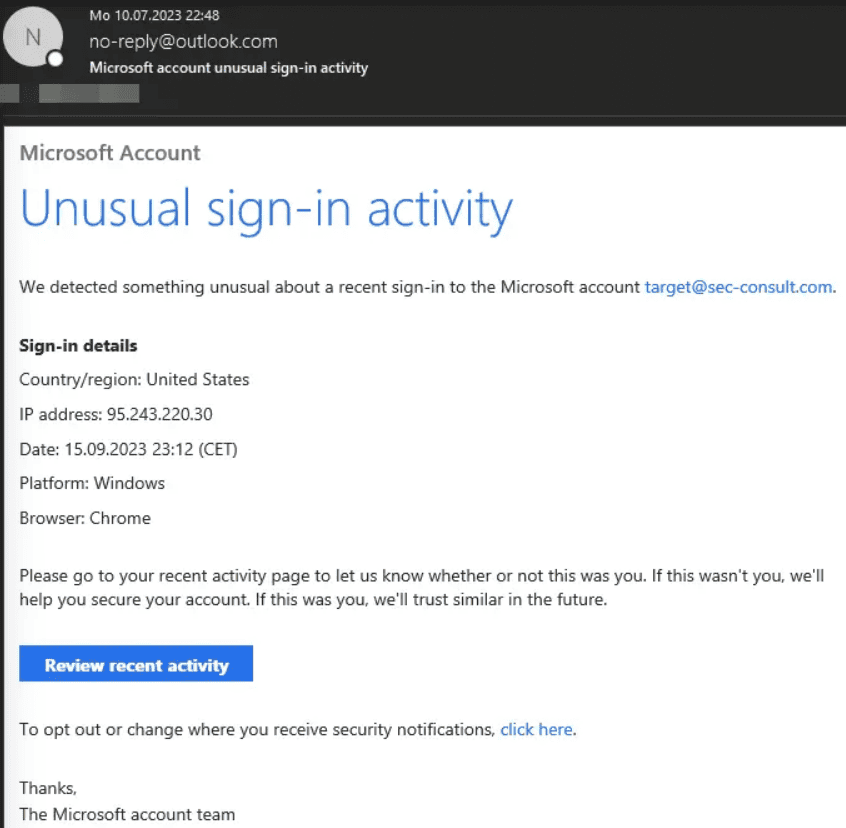
The vulnerability is made possible because SMTP is interpreted in different ways by various messaging services, each of which has added layers of protection on top of the old protocol. Because there is no standardization in that area, email servers sometimes let unwanted mail slip through the cracks if they exploit the gaps between the interpretations. At the same time, not every service SEC Consult tested was vulnerable. Either way, GMX and Microsoft were alerted and have since fixed the problem.
SMTP was never intended for secure communication
Despite several improvements, SMTP has changed relatively little since it was invented in the 1980s. The protocol’s objective was to send digital mail “reliably and efficiently.” Security was not yet a priority, nor was checking for authenticity. After all, in the early days of its usage, SMTP servers were physically present at an organization. With the rise of the Internet, SMTP was suddenly deployed on a much more ambitious scale than it was intended for, resulting in numerous security risks.
Well-known are several vulnerabilities known as “SMTP header injections.” These allow the header of an e-mail to be modified. The results are similar to the proof-of-concept from the above study.
The desire to replace SMTP is anything but new. For decades, experts have been peddling alternatives. Yet even in arguments against the protocol, there is a sense of resignation among its critics. An old ZDnet post put its finger on the problem back in 2005: replacing SMTP is not a technology problem, it just requires the entire world to move away from legacy systems or to accept that it won’t work with later, secure modes of communication.
Most e-mail servers now use STARTTLS, which encrypts communication between two different e-mail servers. Still, with that, the possibility of intercepting mail traffic exists, so there is no end-to-end encryption – nor does it check for the authenticity of servers. There are more security methods that attempt to compensate for SMTP’s shortcomings while maintaining compatibility with legacy services. However, despite the fact that Microsoft continues to add new protocols to its own Exchange Online, the recent research findings show that there are always new vulnerabilities to exploit.
Also read: Qakbot malware returns with phishing attack on hospitality industry
