Notorious state-run hackers from the Lazarus group use the new dangerous CookiePlus malware to gain more persistence on their victims’ systems.
According to security researchers at Kaspersky, Lazarus is running a new campaign called “Operation DreamJob. This attack campaign has been running for five years and initially focused mainly on crypto companies but is now increasingly shifting to IT and defence companies.
In addition, the hacker group also targets nuclear companies. Among others, a nuclear organization in Brazil was attacked, and an unknown organization in Vietnam also fell victim to the malware.
Major malware attack
The recent attacks used a wide range of sophisticated malware, including three custom archive files posing as aptitude tests for IT employees at aerospace and defence companies. Through phishing campaigns on LinkedIn, the attackers gained access to their targets and spread malware.
The attack consisted of multiple phases and used different types of malware, including a downloader, a loader, and a backdoor. The attackers spread the malware using VNC software, a remote desktop viewer for Windows, and another legitimate VNC tool.
In the first phase, a manipulated AmazonVNC.exe file was deployed to install and run the Ranid Downloader. This downloader extracted internal components from the VNC file. Then, in a second archive, a malicious vnclang.dll file was used to load the MISTPEN malware. MISTPEN, in turn, brought in additional malicious payloads, such as RollMId and a new variant of the LPEClient.
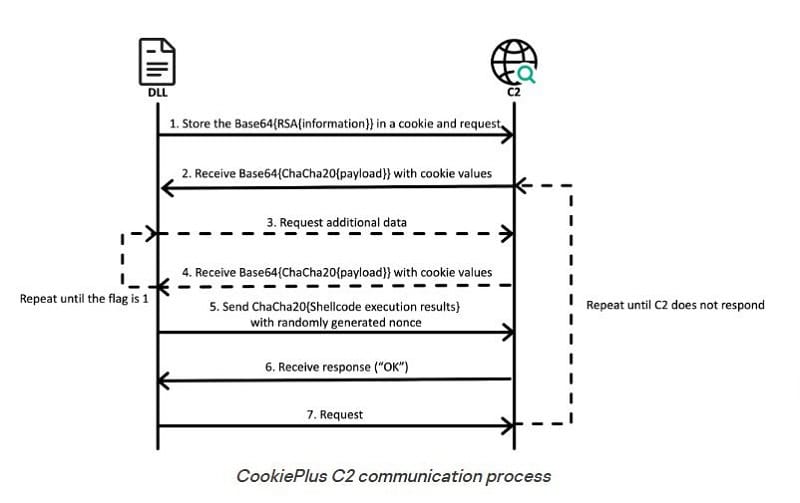
CookiePlus malware introduction
As a final step, the new CookiePlus malware was installed. This disguised open-source plug-in collects system data, including computer name, process IDs and file paths. In addition, CookiePlus causes the main module to go into a “sleep mode” to ensure long-term persistence. The malware can additionally adjust the execution schedule by modifying configuration files.
According to Kaspersky, CookiePlus’s focus on long-term presence in systems makes It a particularly critical threat. This persistence allows Lazarus or others responsible within Operation DreamJob to steal sensitive system data for long periods of time virtually undetected. This data can then be easily used for new operations.
Also read: Lazarus hackers again found passage to Windows kernel