Palo Alto Networks warns of a new malware campaign that uses a seemingly legitimate update to Adobe Flash for cryptojacking.
The campaign was supposed to have been going on at least since August and had a significant peak in activity in September. Researchers at Palo Alto found the threat during a search for Windows executables called AdobeFlashPlayer on servers that are not owned by Adobe.
The fake update software is served up to victims via a credible looking pop-up window in the browser. When a victim clicks through to the download, a message appears saying that an attempt is being made to install software from an unknown publisher. This should alert the victim, but if he or she ignores the warning, a cryptominer is installed on the background.
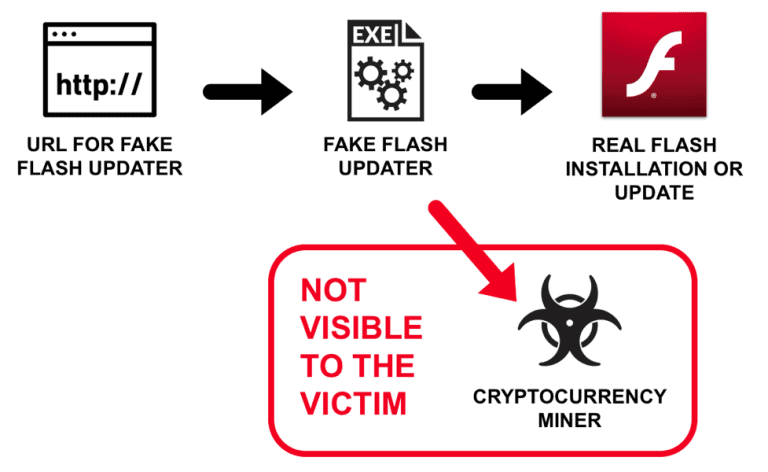
This is an XMRig machine that uses the computing power of the victim’s PC to undetectably mince the Monero crypto coin. In addition, a Flash update is actually downloaded and installed in the foreground, with authentic installation windows, so that the victim is not aware of any harm.
This campaign uses legitimate activity to hide the spread of cryptocurrency miners and other unwanted programs. Organisations with good web filtering and well-trained users have a much lower risk of infection through these fake updates, concludes Brad Duncan, Threat Intelligence Analyst at Palo Alto.
Related: Good IT security does not start with technology, but with people
This news article was automatically translated from Dutch to give Techzine.eu a head start. All news articles after September 1, 2019 are written in native English and NOT translated. All our background stories are written in native English as well. For more information read our launch article.