Check Point security researchers discovered a vulnerability in dronemaker DJI’s software last March. Malicious parties would have access to the drone maker’s accounts, without the need for a password. The hole was closed last September.
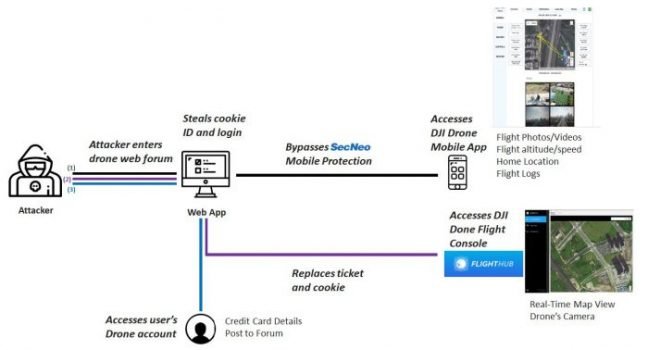
The researchers at Check Point report this in an extensive report about the vulnerability. Due to an error in the software, malicious parties were able to access sensitive information from DJI users. Think of live images taken with the camera of the drones, but also the location of drones, the last four digits of credit card numbers and photos taken during flights. Strikingly enough, in certain situations the attackers could even take control of the drone and plan routes.
Login anywhere
That’s what researcher Oded Vanunu of Check Point tells us. It gave you the ability to give commands to multiple drones, says Vanunu. You could connect a hundred drones together, give them missions and control them automatically, so the hacked account would have to use DJIs FlightHub tool to do that.
The mistake that made all of this possible comes from the DJI forums. These are password-protected, but the Check Point researchers discovered an error in the DJI.com code. This allowed them to run their own JavaScript on the page. That script took the data intended for DJI and sent it to Check Point’s servers. Beneath that were tokens that made it possible to log in. Then it appeared that DJI uses the same tokens to enable login to all accounts. The tokens allowed the researchers to log into all accounts.
A DJI spokesman tells CNet that the vulnerability was reported by Check Point via the bug bounty program. The error was probably never used. DJI is said to have paid several thousand dollars to Check Point, but that did not require payment. DJI researchers viewed the message from Check Point, and marked it in accordance with the Bug Bounty Policy as a high risk, but low probability. It took DJI six months to solve the problem; that time was needed because it had to deal with the entire infrastructure.
This news article was automatically translated from Dutch to give Techzine.eu a head start. All news articles after September 1, 2019 are written in native English and NOT translated. All our background stories are written in native English as well. For more information read our launch article.