A total of 773 million unique email addresses and 22 million unique passwords were dumped online on cloud service MEGA. The dataset, titled Collection #1, contains 2,692,818,238 rows of data coming from different online services.
Security researcher Troy Hunt announces in a blog post that he has been able to download a package of 12,000 separate files on cloud service MEGA. The total amount of data, more than 87 GB, contains email addresses and passwords from different sources.
What I can say is that it contains my own personal data and that it is accurate with a correct email address and password, writes Hunt. In short, if your data is in this leak, chances are that one or more of your passwords will be available online.
Checking online
Hunt discovered the data after several people alerted him to the file. The Collection #1 data dump is also actively discussed at hacker forums according to Hunt.
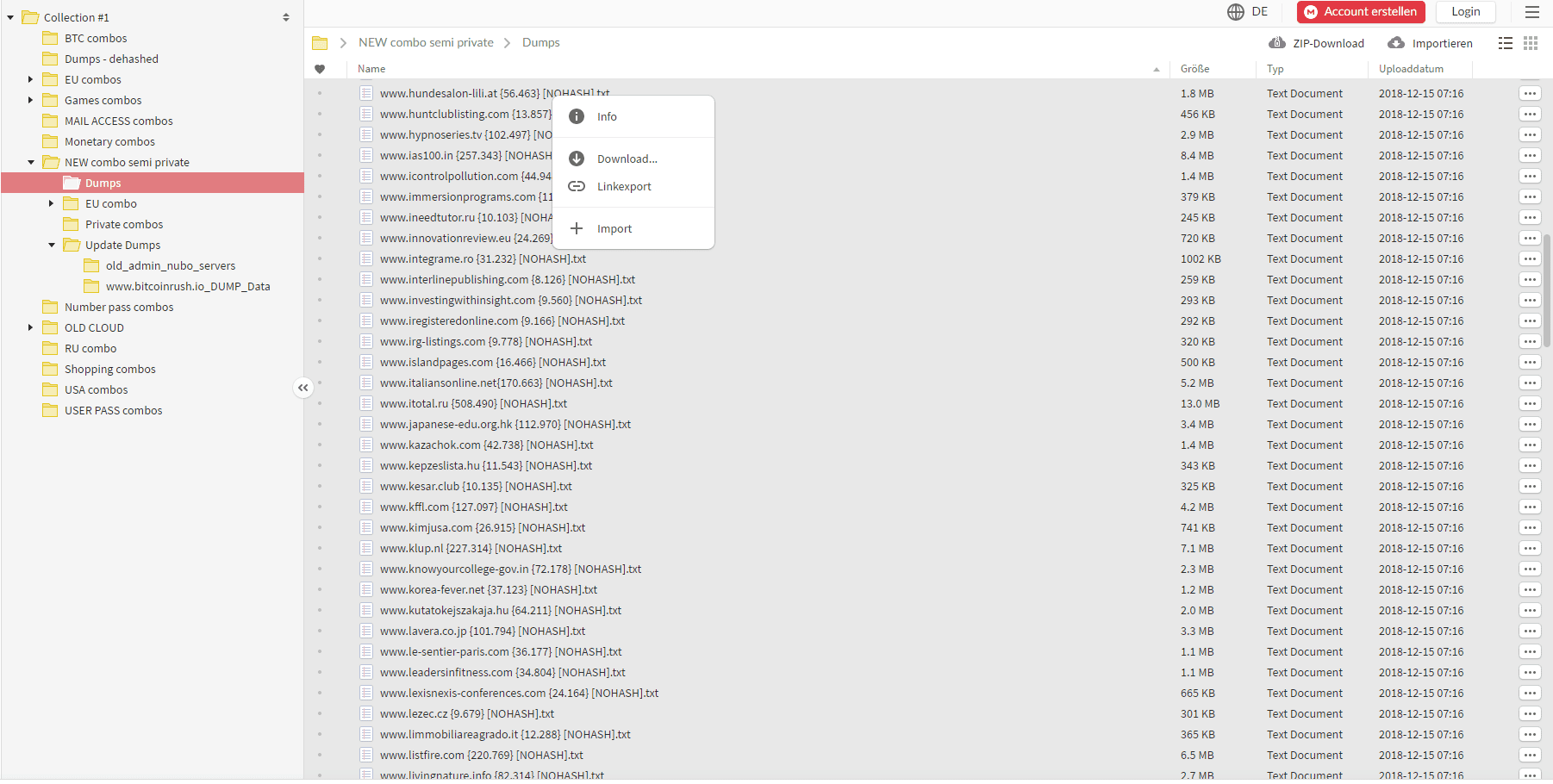
A total of 1,160,253,228 unique combinations of e-mail addresses and passwords are involved. The file contains 772,904,991 unique email addresses and 21,222,975 unique passwords.
The original forum post contains a collection of 2,000+ dehashed databases, sorted by topic with a directory listing of 2,890 files. The collection has now been taken offline, but you can check on Have I Been Pwned to see if your email address is in the collection.
We can’t stress enough how important unique passwords are. Therefore, choose unique passwords for each business-critical application and preferably work with a password manager such as LastPass or 1Password. The latter even has a search function on board that allows you to see which logins have been hacked and urgently need to be replaced. Whenever possible, you always use two-step verification.
Related: These are the 25 worst passwords of 2018
This news article was automatically translated from Dutch to give Techzine.eu a head start. All news articles after September 1, 2019 are written in native English and NOT translated. All our background stories are written in native English as well. For more information read our launch article.