A study of intentionally compromised cloud servers shows that hackers take less than a minute to launch their attacks, and that they continue to do so at a rapid pace from the moment they discover the vulnerable server.
Security company Sophos placed several Honeypot servers in AWS data centres in Ireland, Frankfurt, London and other countries for a month. Honeypots are servers disguised as attractive targets for hackers. Security specialists use them to attract cybercriminals to analyse their behaviour.
Quickly detected
Sophos discovered that it takes an average of 40 minutes before a vulnerable server is attacked, but in some cases malware was at the front door in less than one minute. The rapid response time of the criminals is due to the fact that they also use automated infrastructure. It automatically scans for vulnerable servers and tries to infiltrate them. As soon as attackers gain a foothold within a single server, they try to abuse it in order to penetrate more and more into an organization’s IT infrastructure.
As soon as hackers located a vulnerable server, there was an abundance of attacks. Sophos speaks of an average of thirteen attempts at attack per minute. During the course of the project, which also included the use of servers in other AWS data centres worldwide, the security specialist recorded no less than 5 million attempted attacks.
Own responsibility
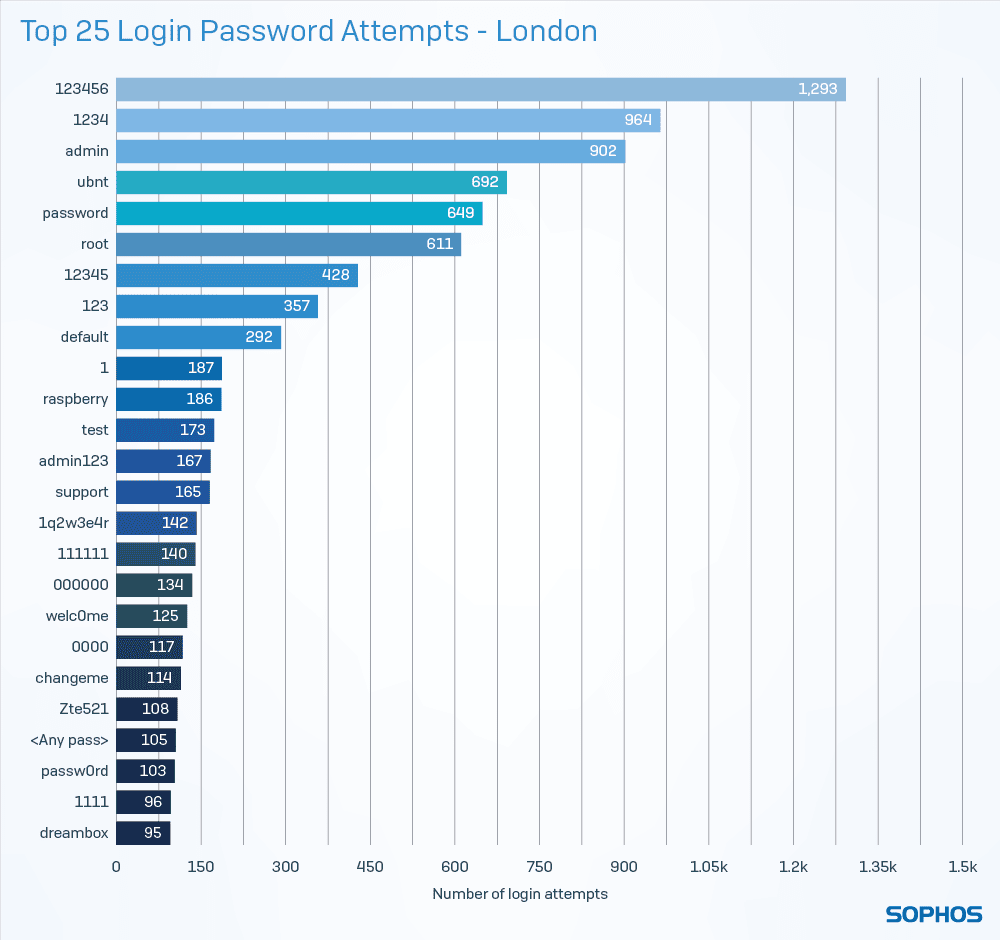
According to Sophos, the study with the honeypots shows how vulnerable public cloud infrastructure is. Moreover, the attacks illustrate the importance of good visibility on the cloud infrastructure, and according to the security specialist, this is often handled too casually today. The public cloud provider is not responsible for the total security of your infrastructure. He makes sure that the platform is closed, but it is up to the user to configure all the services correctly, to set up good policies, to develop detection rules for the deployment of authentication systems and ideally even to pour an AI sauce over the whole to keep an eye on the logs. After all, a hack attempt can be as simple as bombing an exposed login portal with frequently used passwords.
Sophos recorded a lot of such attacks, and used the information to make a nice list of the most tried passwords. If you find yours in the list below, take immediate action and then think about your IT life choices.