Another 17 malicious packages have been discovered in an open-source repository by researchers. In recent times, it has become clearer that these repositories can, have been, and will continue to be used to spread malware.
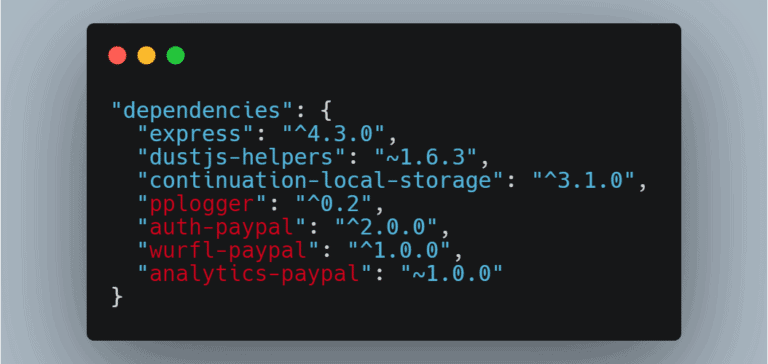
The malicious code was found in NPM, where 11 million developers trade more than 1 million packages with each other. Many malicious packages appear to have originated from different actors who used varying techniques and efforts to trick developers into downloading the compromised packages instead of the safe options.
This discovery is only the latest in a series of similar cases.
Trickery and deception in the repos
The criminals who do this sneak in keyloggers, information stealers, and other kinds of malware designed to extract valuable information that can then be used in hacking campaigns, or just to access anything that could be turned into value. The packages have been sneaked into NPM, RubyGems, PyPi, and other repos.
In many of the examples, the malicious packages have a name that is a single character different from the legitimate package, to confuse people, since we tend to read things in chunks instead of going letter by letter. Often, the malicious packages have the legit code with malware concealed in it like Russian dolls.
Repos are useful but also ripe for abuse
JFrog researchers Andrey Polkovnychenko and Shachar Menashe wrote on Wednesday about the onslaught of malware hosted and delivered through open-source software repos.
The repos have become a delivery vessel for malware distribution. The problem is that repos tend to be trusted resources that do not trigger suspicion from software or users. It is also easy to do installations, making places like NPM prime targets for miscreants.
The malware found is tasked with stealing credentials and information for Discord servers.