Hackers increasingly target Python repositories. Security experts from Check Point recently discovered ten malware packages in PyPi, a popular Python repository.
Malware in Python repositories is typically distributed in familiar-looking packages and highly dangerous. Developers that fall victim unintentionally embed malicious code in their projects. The code may create backdoors and steal credentials.
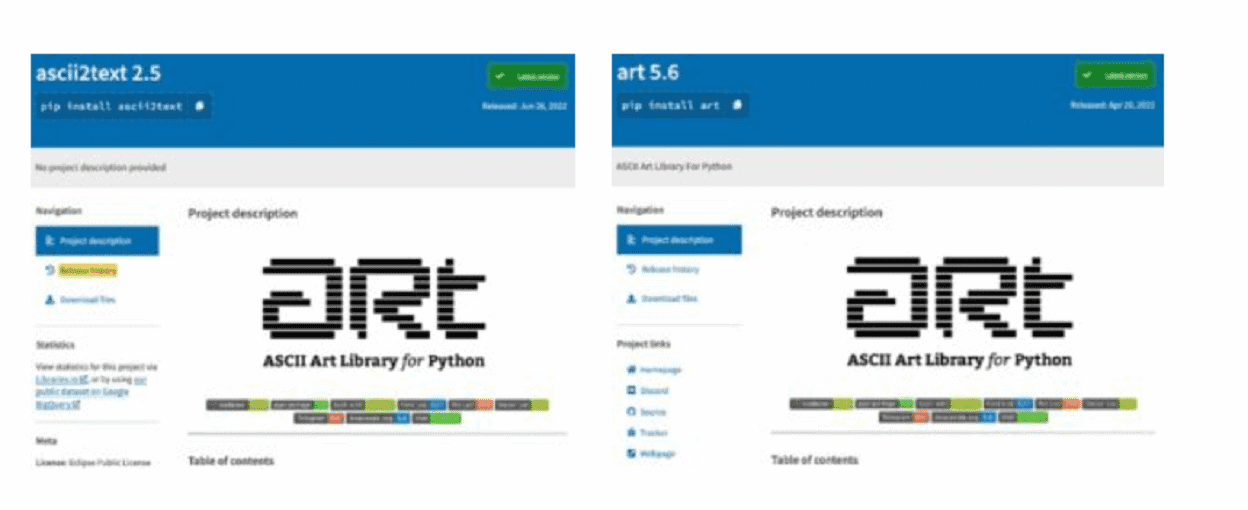
Ten recent malware pacakages
In a recent survey, Check Point found ten new malware packages circulating in PyPi, a popular Python repository. For instance, there’s ascii2text, which imitates a popular ASCII library (art 5.6) and downloads a malicious script that searches web browsers’ local storage for secrets, cookies and crypto wallets. Stolen data is forwarded to a Discord server.
Other malicious packages discovered include pyg-utils, pymocks, PyProto2, test-async, free-net-vpn, free-net-vpn2, zlibsrc, browserdiv and WINRPCexploit.
Supply chain attacks
Malicious Python packages in popular repositories often serve as a setup for supply chain attacks. PyPi isn’t the only distribution channel. Researchers found malicious packages in RubyGems as well.
The amount of users that downloaded the packages is unknown. PyPi has 613,000 active users that use the repository’s code in more than 390,000 projects. PePy, a website that monitors Python project downloads, estimates that most malicious packages get hundreds of downloads.
Tip: Clones laced with malware discovered and purged from GitHub
