The Spring4Shell vulnerability is being abused in large numbers. European companies appear to be favoured among attackers.
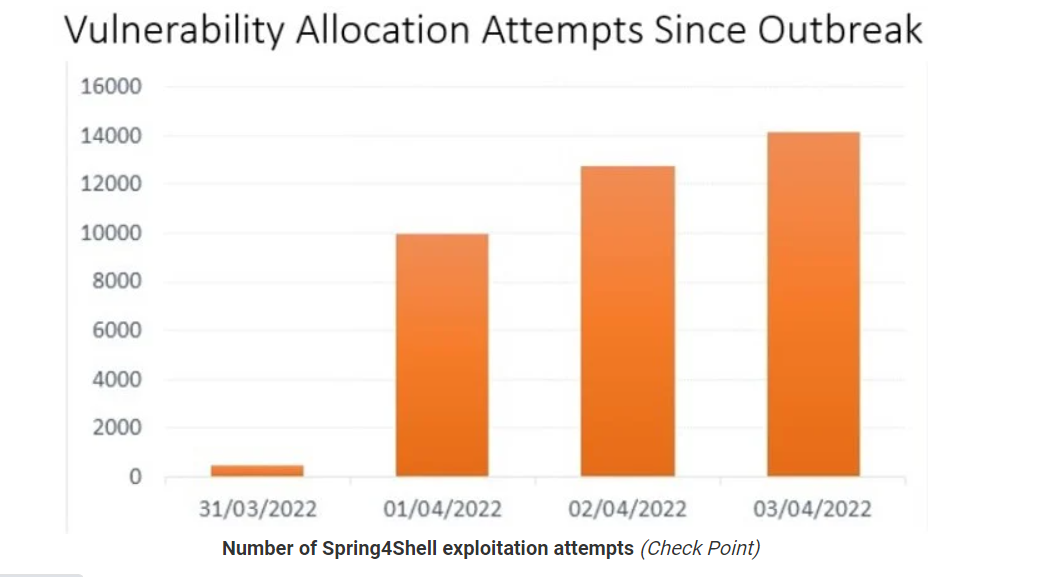
In the first four days following Spring4Shell’s discovery, one in six of those affected had been targeted by hackers. This is concluded by Check Point in a recent report. Telemetry data shows 37,000 remote execution attacks over the past weekend.
Many attacks in Europe
According to the report, software vendors are a particularly popular target. Check Point notes that software vendor breaches can lead to supply chain attacks.
Furthermore, the report shows that European companies are of particular interest to Spring4Shell attackers. About 20 percent of all recorded attacks take place in Europe. The US accounts for 11 percent of attacks.
Cyber watchdog CISA indicates that many of the discovered Spring4Shell attacks target VMware environments. Microsoft environments seem to be of interest as well. Both tech giants released patches and guidelines.
Upgrading to later versions
The Spring4Shell vulnerability affects Spring MVC and WebFlux applications running on JDK9+. All Java Spring environments should be considered a potential attack vector.
Users are advised to upgrade to Spring Framework versions 5.3.18 and 5.2.2 and Spring Boot 2.5.12 which resolved the RCE issue. Users are also advised to watch out for vulnerabilities CVE-2022-22963 and CVE-2022-22947. These vulnerabilities targeted Spring Cloud Function and Spring Cloud Gateway.
