A report by CloudSEK describes how cybercriminals spread a new infostealer through Google Search.
Fake web pages are regularly used to spread malware. Until recently, the Google search results for ‘Windows 11 upgrade’ contained a fake Microsoft website with a fraudulent download link for Windows 11. The website was used to distribute a new infostealer to unknowing victims. Security researcher CloudSEK analyzed the infostealer in a report.
Inno Stealer
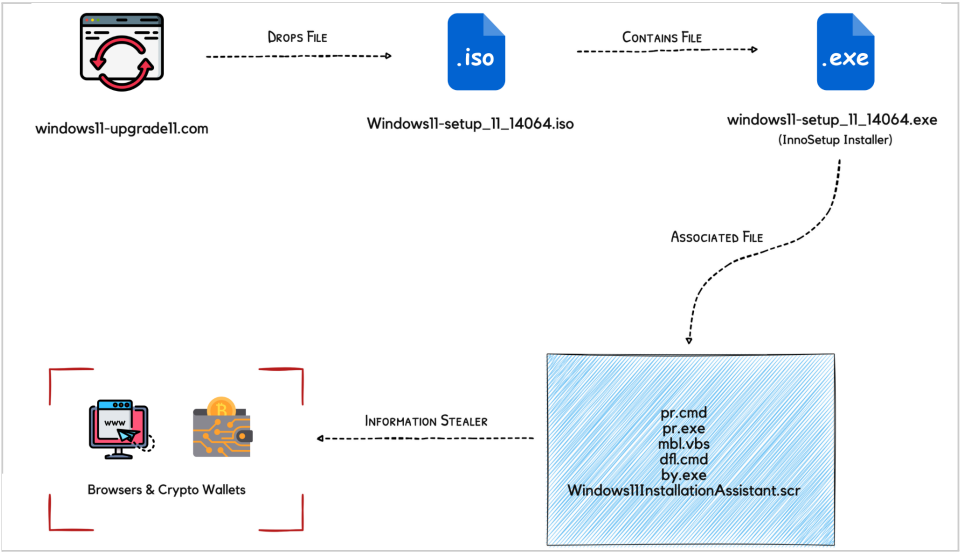
CloudSEK calls the programme ‘Inno Stealer’. This is the first time the infostealer has come to light. The process starts with an executable, disguised as ‘Windows 11 setup’. When running the executable. the programme dumps a temporary file (.tmp) on the disk. From there, the infostealer creates a file in the Startup directory, which starts the program with every reboot. simultaneously, the program uses the CreateProcess Windows API to create four files. This is where the real work begins.
Two of the four files remove security software and disable Windows Defender. The third file functions as a command tool with the highest local privileges. The fourth file contains a script required to execute of the command tool. As local security software is now redundant, the actual infostealer can be deployed.
Inno Stealer creates a file in AppData11InstallationAssistant. The file executes a process that makes local browser cookies, passwords and usernames available to a remote server. Local data is transported to a temporary directory via PowerShell commands. There, the data is encrypted and shipped.
Scale
Inno Stealer is designed for home PCs. Security apps are disabled with local privileges. If a device’s security is managed elsewhere in the network, Inno Stealer has no way of bypassing it. There’s no evidence of Inno Stealer victimizing users in the wild.
