Microsoft is pushing more secure default settings to all Azure Active Directory (AD) users.
Azure AD’s default settings feature a set of basic mechanisms for identity security. These mechanisms include factor authentication (MFA) and security protocols such as Conditional Access and Identity Protection.
The default settings were introduced in October 2019. According to the tech giant, many Azure AD customers have implemented the default settings since then. Microsoft claims these organizations face up to 80 percent fewer hacking attempts than before.
However, Microsoft notes that there are still customers who have not integrated the default security settings. These customers are targeted in a new campaign which pushes the settings to a broader group. Microsoft expects that the campaign brings security to 60 million extra customers.
Implementation process
The campaign will start at the end of June. The tech giant will determine which customers will be the first to receive the security settings based on usage patterns. The target audience includes those who are not yet using Conditional Access, have not yet used security defaults and are not actively using legacy authentication clients.
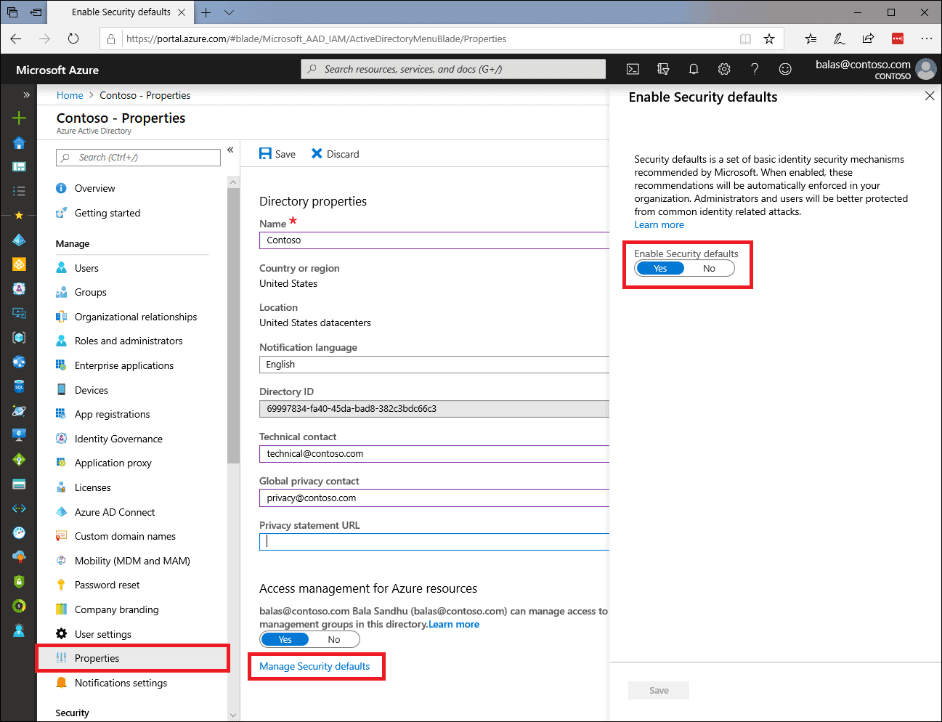
Admins worldwide will be informed by e-mail. From the end of June onwards, they receive a prompt to start the installation process when logging in. Admins can start immediately or opt out through a 14-day ‘snooze’. Upon activation, all users are asked to register for MFA.
Tip: Microsoft emergency update fixes authentication issues in Windows AD
