Security experts recently found a zero-day vulnerability in Microsoft Office. The vulnerability allows malicious PowerShell commands to be executed by opening a Word document.
The vulnerability was named ‘Follina’ and registered as CVE-2022-30190. According to security experts, the vulnerability makes it possible to activate PowerShell commands via the Microsoft Diagnostic Tool (MSDT). Exploits are performed by opening a maliciously modified Word document.
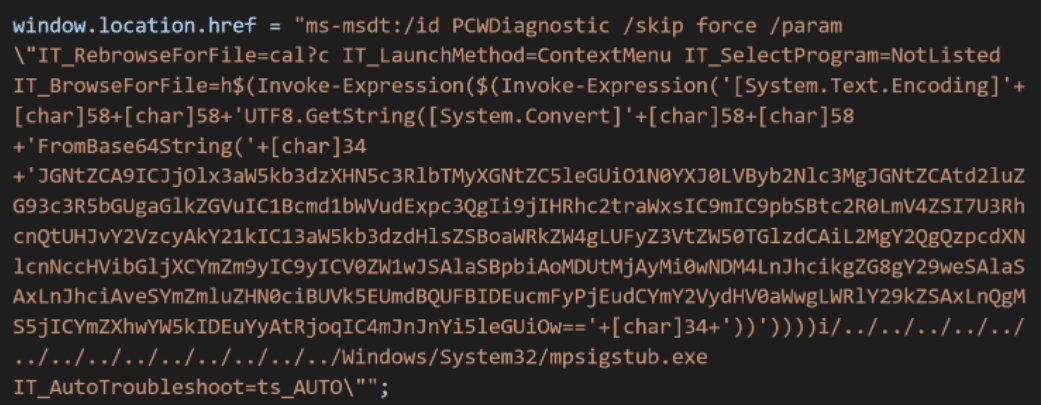
Under the bonnet
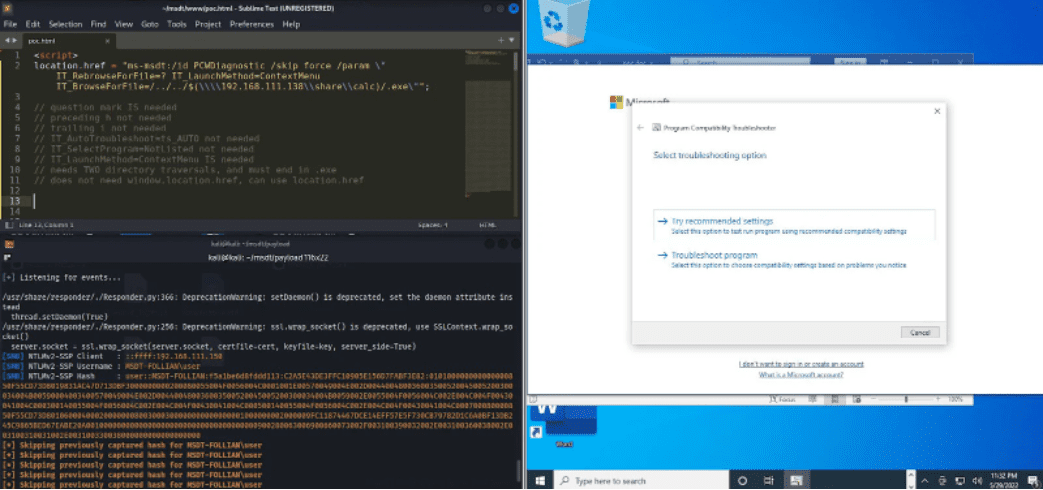
The exploit uses the external link of a Word document to load malicious HTML code. It proceeds to run malicious PowerShell code via the ‘ms-msdt’ scheme. Finally, the PowerShell code causes another malicious packet to be loaded and executed.
Code can even be executed without opening the Word document. The Protected View feature within MS Office is supposed to provide an alert when opening documents that may contain malicious code. By changing the document from a Word file to an RTF format, the security measure is bypassed.
Affected versions are MS Office 2013, 2016, Office Pro Plus from April 2022 onwards (on Windows 11 with the May 2022 updates) and MS Office 2021.
Microsoft responds
Microsoft was notified of the zero-day vulnerability in April. The tech giant initially dismissed the vulnerability as unimportant. Now, a month later, the issue has been addressed with a fix.
