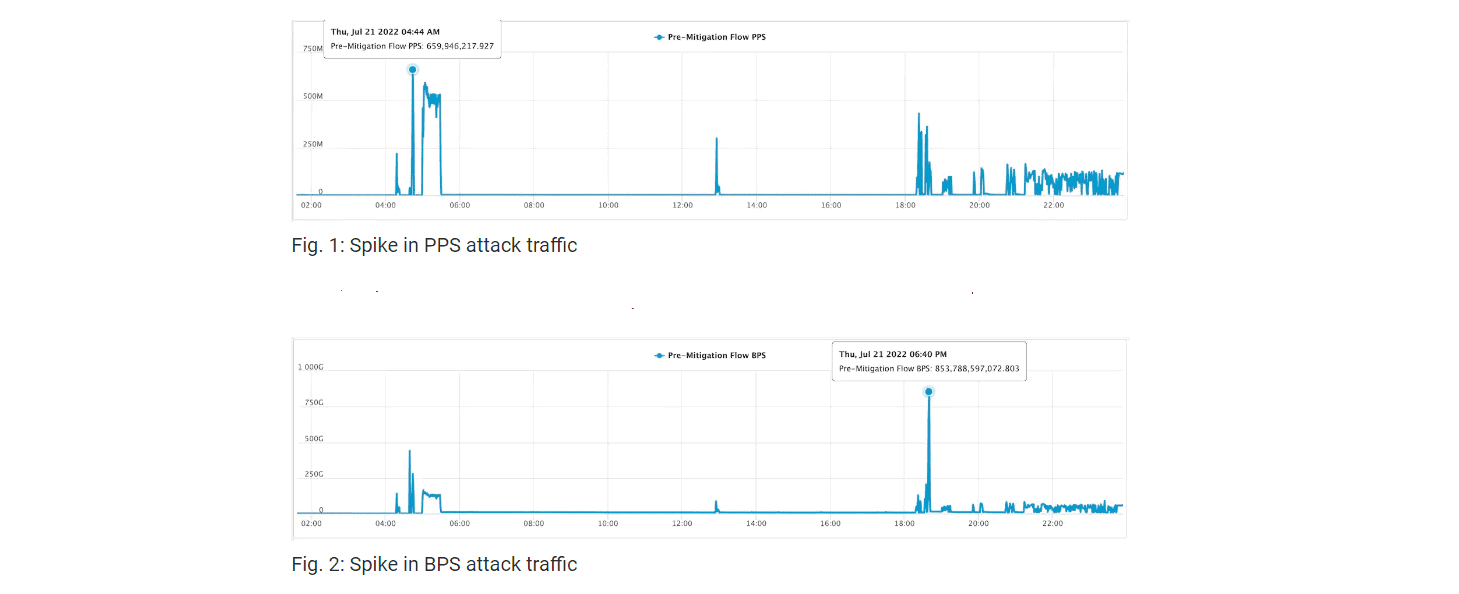
Akamai repelled one of the largest DDoS attacks in European history. Cybercriminals attacked a company with 660 million packets per second (Mpps) and 854 Gbps of data during a 14-hour peak.
According to Akamai, the target company suffered a constant DDoS attack for 30 days. Traffic peaked on 21 July. Akamai recorded 660 million Mpps and 854 Gbps of data during a 14-hour period.
Sophisticated botnet
The investigation revealed that the attackers used an advanced, global botnet. The attack targeted various company IP addresses. Cybercriminels attacked the company 75 times through multiple vectors. Vectors include user datagram protocol (UDP), UDP fragmentation, ICMP flood, RESET flood, SYN flood, TCP anomaly, TCP fragment, PSH ACK flood, FIN push flood and PUSH flood.
Mitigation process
Akamai repelled the attack with its Prolexic platform. This platform consists of 20 high-capacity, global ‘scrubbing centers’. These centers are located close to victims and the sources of DDoS attacks.
The Akamai Anycast network routes malicious traffic to the nearest scrubbing center during an attack. Akamai’s Security Operations Center (SOC) secures or blocks traffic to stop the attack.
A single scrubbing center never processed more than 100 Gbps of data traffic during the recently recorded attack. By distributing traffic, the network withstands enormous attacks.
Tip: Cloudflare fends off largest HTTPS DDoS attack of all time
