Security company Cyble discovered that more than a thousand Virtual Network Computing (VNC) endpoints are unsafely connected to the Internet and open to unauthorized access.
VNC is a platform-independent system that allows users to remotely connect to systems to perform monitoring and adjustments. Users gain access via the remote frame buffer (RFB) protocol.
The method is used in factories, among other locations. Industrial systems without proper security configurations provide easy access to cybercriminals seeking access to an organization’s internal network.
At least 9,000 open VNC endpoints
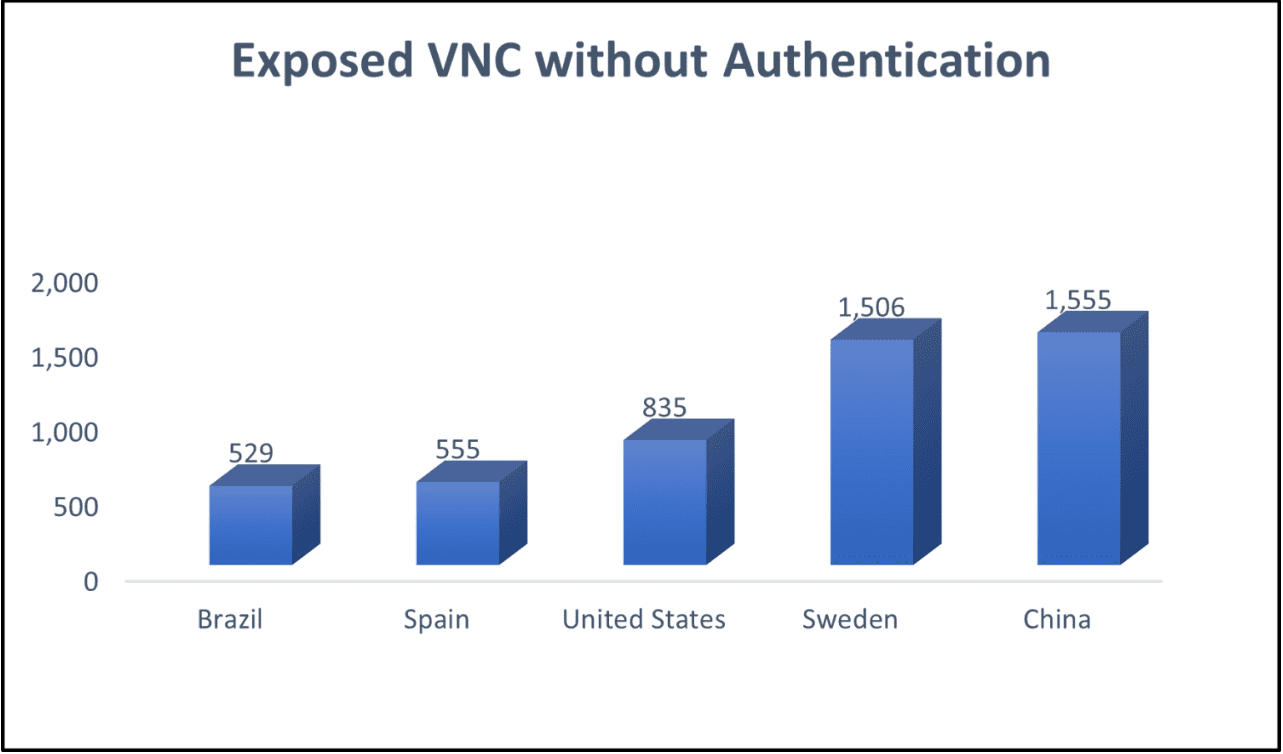
Cyble’s security researchers discovered as many as 9,000 open VNC endpoints or servers. The actual number is likely to be much higher. The open systems found lacked a password and were therefore easily accessible. Most of the open VNC endpoints were found in China and Sweden. Other high-ranking countries were the United States, Spain and Brazil.
The open VNC endpoints include Human Machine Interface (HMI) systems, industrial SCADA systems and workstations. Access to HMI and SCADA systems allows cybercriminals to damage factories and other critical infrastructure environments.
VNC attacks popular among hackers
The study further shows that attacking VNC servers is popular among cybercriminals. The researchers found a high demand for data exposed by VNC systems on dark web forums.
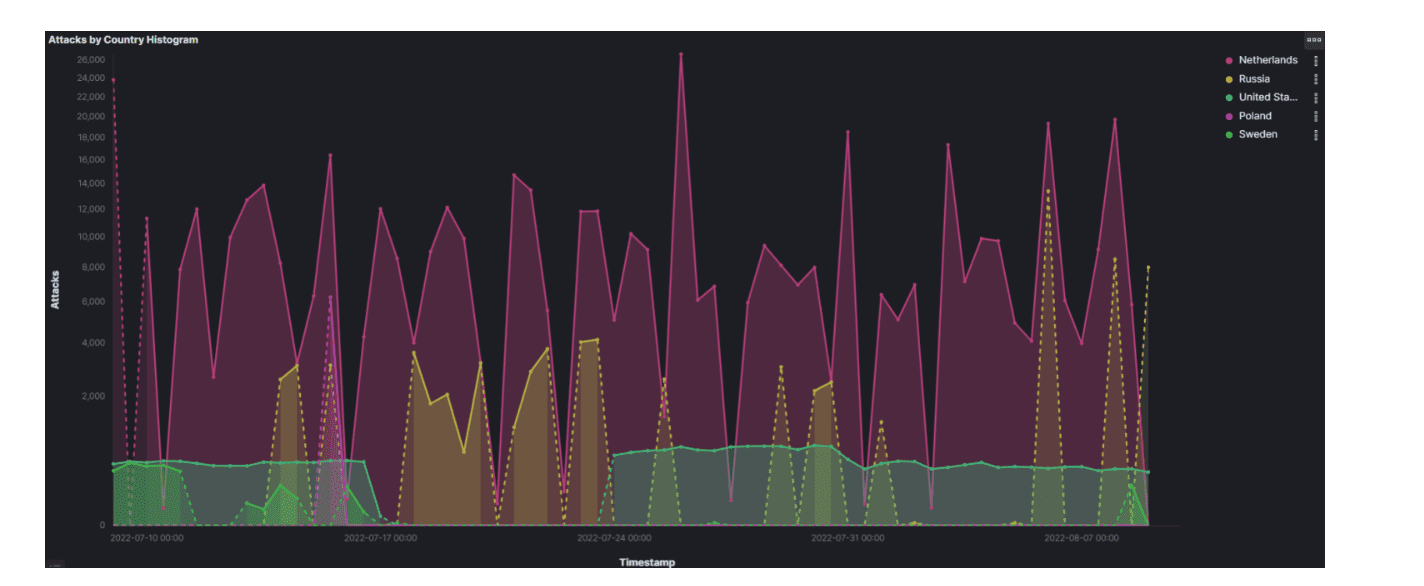
Cyble observed that port 5900, the default port for VNC, received as many as six million requests a month. Most hacking attempts came from the Netherlands, Russia and the United States.
Always password, preferably behind VPN
Cyble urges administrators to properly protect VNC endpoints and servers from cyberattacks. Password security is the bare minimum. Furthermore, administrators of VNC systems are advised to hide servers from the Internet. Servers that have to be internet-facing should run behind a VPN where possible.
Tip: PowerStore, PowerMax, PowerFlex, PowerScale, Object Scale; Dell storage has many flavours